Understanding the Importance of Data Privacy and Security
In today’s interconnected world, data has become one of the most valuable assets for businesses. However, with great power comes great responsibility. Consumers are more vigilant than ever before about how their personal information is collected, stored, and utilized by companies. Data breaches and privacy scandals have eroded trust in brands, highlighting the critical need for transparency and accountability in data handling practices.
Transparency Builds Trust
Transparency is key to building trust with consumers. Brands should clearly communicate their data collection practices, the purposes for which data is used, and the measures taken to protect it. This transparency fosters a sense of control and empowerment among consumers, reassuring them that their information is being handled responsibly.
Compliance with Regulations
Regulations such as the General Data Protection Regulation (GDPR) and the California Consumer Privacy Act (CCPA) have raised the bar for data privacy standards and accountability. Compliance with these regulations is not only a legal requirement but also a demonstration of a brand’s commitment to respecting consumers’ rights. Marketers must ensure that their data collection and processing practices align with the requirements of relevant regulations to avoid fines and reputational damage.
Prioritizing Consumer Consent
Obtaining explicit consent from consumers before collecting their personal data is crucial for maintaining trust and compliance with regulations. Marketers should provide clear and easily understandable consent forms that outline the purposes for which data will be used and offer options for consumers to opt out if they so choose. Respecting consumers’ choices and preferences demonstrates a commitment to ethical data handling practices.
Securing Data Against Cyber Threats
In addition to regulatory compliance and transparency, brands must invest in robust cybersecurity measures to protect against data breaches and cyber threats. This includes encryption, access controls, regular security audits, and employee training on data security best practices. By safeguarding data against unauthorized access and misuse, brands can instill confidence in consumers and mitigate the risks associated with data breaches.
Data Security From a Private Equity Perspective
From a private equity perspective, the significance of data privacy and security in digital marketing cannot be overstated. As investors assess potential targets or portfolio companies, they increasingly scrutinize data handling practices as a critical aspect of risk management and value creation. Brands that prioritize transparency, compliance, and trust not only mitigate regulatory and reputational risks but also enhance their attractiveness to investors. Private equity firms recognize that robust data privacy and security measures not only safeguard consumer trust but also contribute to the long-term viability and value of their investments. By aligning with regulatory requirements, obtaining explicit consumer consent, and implementing stringent cybersecurity protocols, companies can demonstrate their commitment to responsible data management practices, ultimately bolstering their appeal to investors and stakeholders alike.
Conclusion
In an era defined by data-driven marketing, prioritizing data privacy and security is no longer optional—it’s a business imperative. By prioritizing transparency, compliance with regulations, obtaining consumer consent, and implementing robust cybersecurity measures, marketers can build trust with their audience and differentiate themselves in a crowded marketplace. Embrace data privacy and security as core pillars of your digital marketing strategy and pave the way for long-term success in the digital age. Contact us to learn more.
In a world where the digital battleground is ever-evolving, the way we visualize cyber threats is more than just a matter of aesthetics. It’s about conveying a message that resonates with the complexity and urgency of the challenges we face. Over the years, cybersecurity branding has gone through various phases, from the ominous figures in dark hoodies to monstrous depictions of malware. But now, a new trend is emerging—one that’s straight out of a science fiction saga.
The Evolution of Cyber Security Symbolism:
Let’s take a quick trip down memory lane to understand how cybersecurity brands have evolved in their visual language:
- The Hooded Figures: Once upon a time, cybersecurity brands leaned heavily on the stereotype of hackers as mysterious figures cloaked in darkness, lurking in the shadows of the digital realm. While this imagery effectively conveyed the sense of a hidden threat, it also perpetuated stereotypes and failed to capture the true nature of cyber adversaries.

- Abstract Digital Art: In this phase, cybersecurity brands leaned towards abstract digital art to represent cyber threats. They utilized geometric shapes, neon colors, and glitch effects to convey the complexity and unpredictability of digital vulnerabilities. While visually captivating, this approach sometimes lacked a clear connection to the real-world implications of cyber attacks.

- Monstrous Malware: As the threat landscape expanded, so did the imagery associated with cyber threats. Brands began depicting malware as monstrous creatures, embodying the destructive potential of cyber attacks. While this approach added a layer of visual interest, it often bordered on the cartoonish and failed to convey the sophistication of modern cyber threats.

But now, a new era has dawned in the world of cybersecurity branding—one that draws inspiration from the boundless realms of science fiction. Enter the age of Sci-Fi Inspired Branding.
Incorporating elements from the vast expanse of the cosmos, cybersecurity brands are embracing a visual language that speaks to the futuristic nature of the challenges we face. Here are some examples of websites that are boldly venturing into this new frontier:
- SecurityScorecard: With its sleek interface and futuristic aesthetic, SecurityScorecard’s website feels like something straight out of a cyber-thriller video gam. The use of dynamic visuals and futuristic typography conveys a sense of innovation and technological prowess. Check out how Bluetext contributed to this brand revolution.
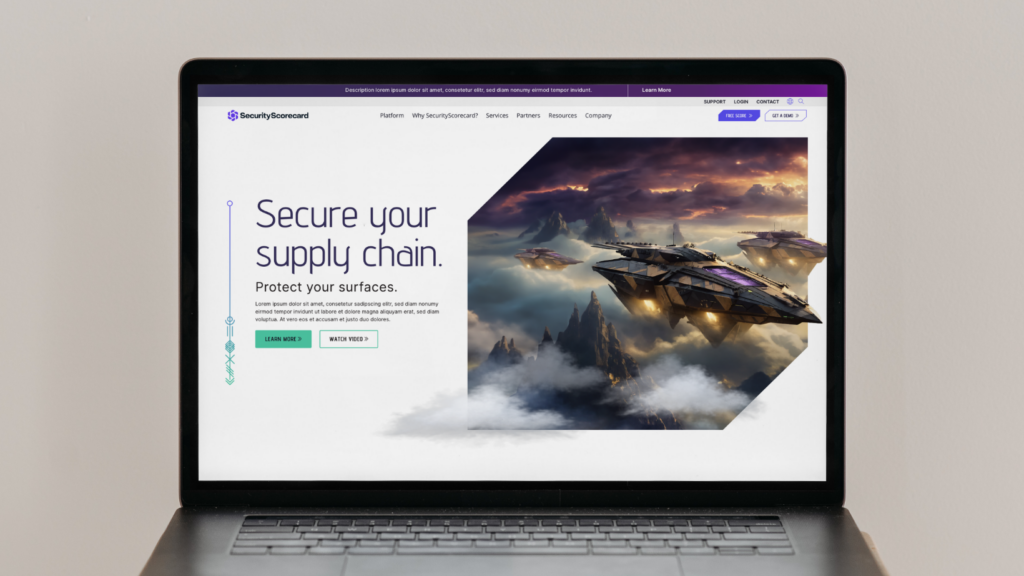

- Cybereason: Cybereason’s website takes visitors on a journey through the digital universe, with swirling nebulae and sleek spacecraft serving as the backdrop for its cybersecurity solutions. The use of space-themed imagery reinforces the brand’s message of protecting against unknown threats from the far reaches of the digital universe.

- CrowdStrike: As you scroll through CrowdStrike’s website, you’re greeted with a cast of characters straight out of a sci-fi epic—space cowboys and invaders battling it out against a backdrop of cosmic chaos. This playful yet powerful imagery captures the essence of the cyber threat landscape while injecting a sense of adventure into the brand’s messaging.


- Darktrace: Darktrace’s website transports visitors to a futuristic landscape filled with shimmering data streams and pulsating energy fields. The use of sleek, metallic textures and holographic interfaces creates an immersive experience that reflects the cutting-edge nature of the company’s AI-driven cybersecurity solutions.

- SentinelOne: SentinelOne’s website features sleek spacecraft navigating through asteroid fields and alien landscapes. The use of dynamic animations and sci-fi-inspired imagery reinforces the brand’s message of protecting against next-generation cyber threats.

- Varonis: Varonis’ website features sleek, robotic figures that rise against a futuristic backdrop. The use of sci-fi-inspired visuals and dynamic animations creates a sense of immersion, highlighting the company’s innovative approach to data security and threat detection. Varonis’ website captures the imagination and reinforces the brand’s message of protecting against cyber threats in the digital age.

As the line between science fiction and reality is becoming increasingly blurred, it’s only fitting that cybersecurity brands embrace the boundless possibilities of the sci-fi universe. By infusing their visual identity with elements from the farthest reaches of space, these brands are not only staying ahead of the curve but also inspiring a sense of wonder and imagination in their audiences.
So, the next time you find yourself navigating the digital wilderness, remember that the guardians of cyberspace are not just warriors—they’re spacefaring adventurers on a mission to protect the frontiers of the digital realm.
The cybersecurity market is ever-evolving, and with it, digital marketing strategies should anticipate these trends and adapt to stay ahead of them. Careful market analysis and years of industry expertise amongst Bluetext marketing specialists reveal AI technology, increased investment from SMBs, and enterprise risk quantification are expected to impact cybersecurity provider marketing strategies in 2024.
Cybersecurity Trends to Watch:
Artificial Intelligence is Impacting All Industries — Including Cybersecurity
We’ve seen AI headlines not just in the Tech markets, but all over the mainstream media. As utilization of AI becomes more prevalent, with access to open-source models like ChatGPT, cybersecurity providers will need to develop entirely new standards of trust. Organizations will be seeking cybersecurity providers to ensure they can securely deploy AI technology. On top of that, malicious uses for AI will increase the need for protection against cyber attacks. Cybersecurity providers will need to speak to their ability to deploy safe AI product features while also promoting their ability to protect against these AI-powered attacks.
Check out how Bluetext client AmeliaAI leverages conversational AI as a tool for business optimization.

SMB Organizations are Investing More in Cybersecurity
Managed services are becoming an increasingly important purchase for small and medium-sized businesses. Security attacks on SMBs are felt deeply throughout the organization, compared to large enterprises that may find more protection in silos and sheer size. The good news is that, because of increased awareness of this vulnerability, SMBs’ spending on cyber security is expected to reach $109 billion worldwide in 2026. Cybersecurity providers should take advantage of this growing customer base and make additional considerations for SMB target audiences when designing digital marketing strategies.
Enterprises Are Seeking Better Quantification of their Cybersecurity Risks
For enterprise decision-makers, their willingness to invest in cybersecurity measures will hinge on the ability to accurately quantify their current risks. According to Gartner, turnover in the CISO position is an increasing threat to enterprises; they expect 50% of cybersecurity leaders will have left their positions by 2025. A large contributor to CISO stress is a lack of organizational support for seeing cybersecurity measures as a crucial element of meeting business objectives. Calculating the degree of security risk at an enterprise will play a key role in getting organizational buy-in for increased cybersecurity measures. Marketing strategies will need to speak to both cybersecurity leaders (who are looking to fortify their security measures) and executives (who are looking to advance business goals).
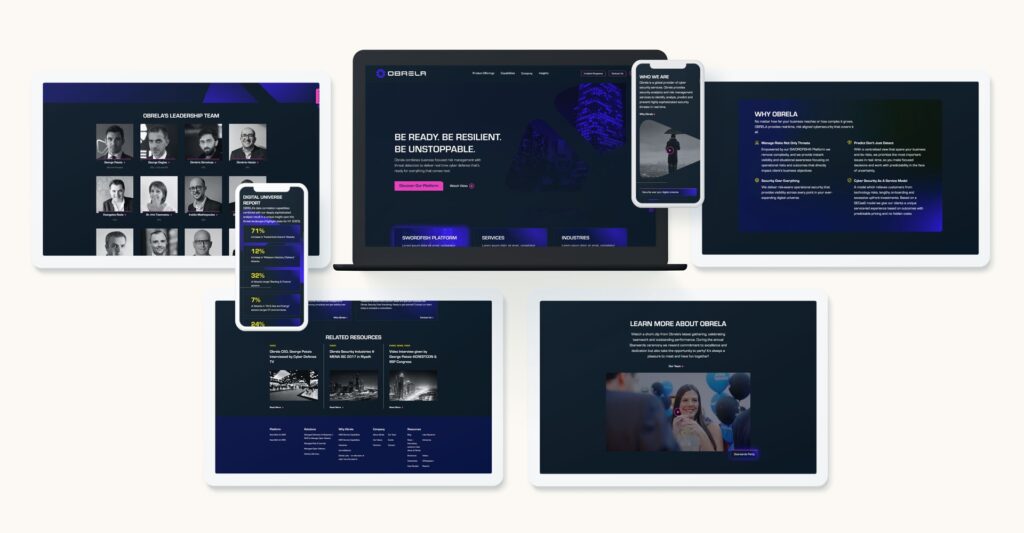
Check out our recent work with Obrela, a world-class cyber security provider, who came to Bluetext for support in updated brand, logo, messaging, website, and video to connect with technical and executive-level audiences.
A digital marketing agency can help your company stay on top of the latest trends in cybersecurity and figure out a plan for how to address these trends in your overall marketing strategy. At Bluetext, we specialize in working with industry-leading cybersecurity professionals; see how we work with companies to build credibility in the realm of cybersecurity in this recent blog.
Curious about what other trends we expect to see in the upcoming year? Read our blog on the 2024 Future Forecast from Bluetext.
In the competitive world of cybersecurity, standing out in search engine results is crucial. However, achieving high rankings requires a unique approach tailored to the industry’s nuances. In this blog post, we’ll explore SEO strategies specifically designed for cybersecurity brands.
1. Secure and Mobile-Friendly Websites
Search engines prioritize secure and mobile-friendly websites. Ensure that your site is HTTPS secured, providing a safe browsing experience. Mobile responsiveness is also a crucial factor, considering the increasing use of smartphones for online activities.
When designing new websites for our clients, we subscribe to a mobile-first mentality, ensuring any new website design works seamlessly on mobile devices. Take our work with Securonix for example. Securonix delivers a next-generation security analytics and operation platform for the modern era of big data and cyber threats. They came to Bluetext to evolve their brand and website with a completely new look. One of the major components of the rebuild of the Securonix website was to ensure every part of the website looked and worked seamlessly on various mobile devices across multiple browsers. Bluetext did extensive regression and cross-browser testing to ensure all pages and functionality were rendered and functioned as intended.
2. Targeted Keyword Optimization
Identify and optimize for relevant keywords specific to cybersecurity. Tailor your content to address common queries and concerns in the cybersecurity landscape. Long-tail keywords that reflect user intent can be particularly effective in attracting the right audience.
A key deliverable in any Bluetext website design and development engagement is the creation of an SEO roadmap, identifying keywords to be implemented across the website including headlines, blog posts, and navigation menus.
3. Quality Content with Expertise
Create high-quality, authoritative content that showcases your expertise in cybersecurity. This can include in-depth articles, whitepapers, and case studies. Valuable content not only attracts organic traffic but also positions your brand as a trusted source of information.
When developing a new website for our clients, we always recommend developing a robust blog program to establish brand credibility and increase SEO on-page ranking. If clients don’t have the resources in-house to create blog content, we’re happy to do so on their behalf as part of our engagement, ensuring the utilization of the correct SEO keywords and topics.
4. Technical SEO Best Practices
Implement technical SEO best practices, such as optimizing meta tags, improving website speed, and enhancing site navigation. Search engines reward websites that provide a smooth and user-friendly experience.
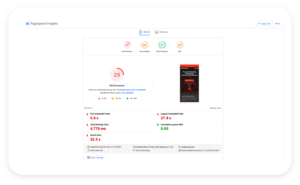
One tool you can utilize is Google’s PageSpeed Insights. You can analyze your existing website and determine ways to improve your technical SEO score, boosting your on-page search results.
5. Backlinks from Trustworthy Sources
Build a strong backlink profile by obtaining links from authoritative and trustworthy sources within the cybersecurity domain. Collaborate with industry influencers, participate in cybersecurity forums, and contribute to reputable publications to earn quality backlinks.
6. Regular Security Audits
Perform regular security audits not only for the safety of your users but also for SEO. Search engines may penalize insecure websites. By maintaining a secure online environment, you not only protect your users but also ensure your site’s visibility in search results.
7. Local SEO for Targeted Reach
If your cybersecurity brand operates in specific regions, leverage local SEO strategies. Optimize your Google My Business profile, include location-specific keywords, and participate in local cybersecurity events to enhance your presence in local search results.
By combining these SEO strategies tailored for cybersecurity, you can not only improve your search engine rankings but also establish your brand as a go-to resource for users seeking reliable and secure solutions in the digital realm. Need support in developing your SEO strategy? Contact Bluetext for help.
Influencer marketing is a buzzword across industries, but how does it fare in the realm of cybersecurity? In this blog post, we’ll delve into the potential and challenges of influencer marketing for cybersecurity brands.
1. Identifying the Right Influencers
In the cybersecurity space, authenticity is key. Look for influencers who not only have a substantial following but also possess genuine expertise in the field. A cybersecurity influencer should be able to speak knowledgeably about your product and its benefits.
2. Educational Collaborations
Collaborate with influencers on educational content. Webinars, live sessions, or joint blog posts that provide valuable insights into cybersecurity trends and solutions can be mutually beneficial. This not only promotes your brand but also enhances the influencer’s credibility; a win-win situation for both parties.
3. Authentic Endorsements
In the world of cybersecurity, trust is paramount. Ensure that influencers authentically endorse your product based on its merits. Genuine recommendations resonate more with the audience and contribute to building trust in your brand as well as the authenticity of the influencer.
4. Thought Leadership Partnerships
Align your brand with influencers who are considered thought leaders in cybersecurity. Their endorsement not only boosts your credibility but also positions your product as a cutting-edge solution in the eyes of your target audience.
5. Addressing Trust Concerns
Be mindful of potential trust issues that may arise. Clearly communicate any influencer partnerships to your audience, emphasizing the shared values and commitment to cybersecurity. Transparency is crucial in maintaining the trust you’ve worked hard to build.
6. Metrics and Measurement
Define clear metrics to measure the success of influencer collaborations. Whether it’s increased website traffic, engagement on social media, or conversions, having quantifiable goals ensures that your influencer marketing efforts align with overall business objectives.
Influencer marketing in cybersecurity can be a powerful strategy if approached with authenticity and strategic thinking. By choosing the right influencers and maintaining transparency, you can leverage their reach to enhance your brand’s credibility and reach a wider audience.
Interested in learning more about the power of influencer marketing and how it can impact your marketing strategy? Contact us here at Bluetext.
Social media isn’t just for sharing cat videos and memes; it’s a powerful tool for cybersecurity marketing. In this blog post, we’ll explore how marketers can leverage social media platforms to promote cybersecurity solutions effectively.
1. Educational Content
Use social media to share bite-sized, educational content about cybersecurity threats and best practices. Infographics, short videos, and quick tips engage your audience and position your brand as an informative resource. Short-form content is also easily digestible for your audience and can be shared easily across multiple social platforms with relative ease.
2. Interactive Webinars and Live Sessions
Host live webinars or Q&A sessions on platforms like Facebook or Instagram. This not only provides valuable information to your audience but also allows for direct interaction, building a personal connection between your brand and potential customers.
3. Cybersecurity Challenges and Quizzes
Create interactive challenges or quizzes related to cybersecurity on platforms like X or Instagram. Engaging content not only attracts attention but also educates your audience in a fun and memorable way.
4. Highlight Security Features
Use platforms like YouTube to create video content showcasing the security features of your products. Seeing is believing, and visual demonstrations can be powerful in conveying the effectiveness of your cybersecurity solutions.
Check out this product essence video we created for cybersecurity startup, Phosphorus, bringing their product to life in a creative yet informative way.
5. Partner with Influencers
Collaborate with influencers in the cybersecurity space to amplify your reach. Influencers can provide authentic endorsements and reach audiences that may be otherwise challenging to access through traditional marketing channels.
By strategically utilizing social media, cybersecurity marketers can connect with their audience, educate them about the importance of security, and establish a strong online presence. To learn more about developing a captivating social media strategy in the cybersecurity industry, contact us.
In the ever-evolving world of cybersecurity, building trust is not just a goal—it’s a necessity. As a marketer in this space, your success hinges on how well you can communicate credibility to your audience. In this blog post, we’ll explore some effective strategies to instill trust in your cybersecurity marketing efforts.
1. Establish Thought Leadership
Position your brand as an authority in the cybersecurity domain. Regularly publish insightful content, participate in industry discussions, and showcase your expertise. This not only demonstrates credibility but also attracts an audience seeking reliable information.
2. Transparent Communication
In a field where transparency is paramount, be open and honest about your products and services. Clearly communicate how your solutions work, what security measures are in place, and how you handle data. Transparency fosters trust, and trust builds lasting relationships.
3. Leverage Customer Testimonials
Nothing speaks louder than satisfied customers. Feature case studies and testimonials from clients who have successfully navigated cybersecurity challenges with your solutions. Real-world success stories provide tangible evidence of your product’s effectiveness.
In the design and development of a new website for cybersecurity startup, Waratek, our team recommended featuring case studies clearly in the navigation menu, ensuring easy access for users.
4. Stay Ahead of Trends
The cybersecurity landscape is dynamic, with new threats and technologies emerging constantly. Showcase your commitment to staying ahead of the curve by addressing the latest trends, challenges, and solutions. This positions your brand as forward-thinking and adaptive.
When developing a new website for our clients, we always recommend developing a robust blog program to establish brand credibility and increase SEO on-page ranking. If clients don’t have the resources in-house to create blog content, we’re happy to do so on their behalf as part of our engagement, ensuring the utilization of the correct SEO keywords and topics.
5. Engage in Community Building
Build a community around your brand where users can share experiences, ask questions, and learn from each other. A vibrant community not only fosters a sense of belonging but also provides potential customers with real insights into your product’s efficacy.
Chatbots are a great way to engage with your community, ensuring you can provide customized feedback and answers to their questions at the click of a button. An FAQ page can also be helpful if you find yourself having to answer the same question time and time again.
6. Certifications and Compliance
Highlight any relevant certifications and compliance standards your cybersecurity products adhere to. This not only demonstrates your commitment to industry best practices but also reassures customers that your solutions meet the highest security standards.
In conclusion, trust is the currency of the cybersecurity realm. By incorporating these strategies into your marketing efforts, you can establish and reinforce credibility, ultimately paving the way for long-term success.
Are you interested in learning more about building trust with your target customers and establishing brand credibility? Contact us here at Bluetext to learn more.
2 years ago SonicWall approached Bluetext with a campaign challenge: “Help us infuse originality within an over-saturated cybersecurity market. Portray Boundless Cybersecurity ability to break free of cyber threats.”
Bluetext’s response? Hours upon hours huddled over brainstorming sessions until the winning idea came to light. Portraying the end-users in a surrealist, anti-gravity state in which they quite literally “break free” from the constraints and anxieties of impending threats. But how could this be done? With a troupe of ballet dancers, a giant trampoline, and an imaginative team of creative & strategic minds the first Boundless photoshoot was made possible.

By knowing the unknown, providing real-time visibility, and enabling breakthrough economics, SonicWall protects against boundless exposure points for increasingly remote, mobile, and cloud-enabled workforces. In order to communicate SonicWall’s business values across a variety of businesses, Bluetext prescribed a verticalized approach to target the unique needs of each industry. Every detail, from costume to backdrop, was personalized to resonate with distinct audience personas. To truly stand out and earn attention in a crowded cybersecurity arena, the campaign centered on fantastical floating imagery, which served to visualize an anti-gravity feeling of breaking free of cyber threats. To achieve this vision, action photography of models jumping and free-falling atop a giant trampoline was captured. With custom photoshoots, expert post-production editing, and head-turning taglines Bluetext truly elevated the campaign to new heights. As a collection, the campaign imagery showcased SonicWall’s wide range of customer success, and as individual targeted campaign assets, the images emphasized SonicWall’s application to industry-specific use cases. New website pages, banner ads, and social graphics were developed to reinforce ”When Cyber Threats Are Limitless, Your Defenses Must Be Boundless.”

The campaign was a roaring success. So much so that it inspired a Boundless 2.0 campaign that elevated key art imagery to 3D video production to tell the evolving Boundless story. This time, the campaign focused on the end user’s journey into a surrealist, anti-gravity state of mind. The campaign video spans a variety of industry applications, from higher education libraries to retail shops, but focuses on the perspectives of an SMB and remote employee. The narrative describes the current state of cybersecurity, being a sense of closed-off isolation to avoid the fear of cyber threats, but begs the question of ‘what if?’ The main characters are shown proceeding through their daily responsibilities (whether that be commuting into the office, or multi-tasking child care responsibilities at home) until interacting with SonicWall products on their given devices. As these users connect to SonicWall they experience the unconventional possibilities of cybersecurity; ‘What if cybersecurity felt…free?’ The characters are transitioned to a surrealist Boundless world, in which 3D video effects bring a state of gravity-free liberation from constraints of the past. The characters “break free” to realize a more secure, yet freer, future with SonicWall.
To further compliment the Boundless 2.0 campaign video, Bluetext brought the story to life on the SonicWall website homepage and campaign landing page. Both of which feature 3D video in the hero zone to showcase Boundless Cybersecurity for both the remote and in-office workforce. Bluetext animators built a custom 3D environment for each character, which is showcased through 360 pan-around camera effects. Attention to detail was everything, from the outfits worn by the character to the interior decor with hints of the SonicWall brand elements. The characters themselves even parallax for hyper-realistic body motion. The rest of the pages were designed by the Bluetext website & UX designers to highlight the campaign’s core messaging, featuring new products and industry-related use cases.

In an impressive feat of animation, website design, videography, and most of all creative brainpower, Bluetext accomplished its challenge. The Bluetext and SonicWall team combined forces to bring new energy and direction to the SonicWall Boundless Cybersecurity campaign. In two years the campaign has evolved to new heights, but just like SonicWall security, the potential is boundless. Stay tuned to see how the campaign further evolves in 2022, and contact us to see how we can develop a state-of-the-art campaign for you.
Picture this: You’re a cybersecurity expert with a next-generation product or service, and you’re looking for a way to get your message into the market uniquely. The industry landscape is crowded with companies with similar offerings and limited ways to stand out. You’ve been researching for hours and finally come across the perfect blog post – one about why brand storytelling is critical in cybersecurity (hint: you’re reading it). Now that you’ve found a blog post that answers your branding questions, you’re wondering where to find a cybersecurity marketing agency; in that case, I have some good news for you.
Sit back, enjoy a warm cup of coffee, and keep reading to learn more about the importance of brand storytelling through some of our favorite examples in cybersecurity.
Why Is Brand Storytelling in Cybersecurity Important?
The cybersecurity market is growing by approximately 10% every year. As a cybersecurity marketing firm, Bluetext has witnessed this growth and know it’s becoming harder to stand out in the cyber arena. These days, saying you solve your customers’ problems, and that your solutions are the best, simply isn’t enough. B2B buyers are tired of the same experience and are looking for authenticity and some sort of a connection. Even in a highly technical industry, it’s important to recognize your customers are still human! This is where brand storytelling comes in to help. Stories are an incredibly powerful tool in human connection and research shows the human brain positively responds to the impact of stories. Reading, seeing, and hearing a story is a way for users to enter the experience and connect with the subject of the story. By connecting with a story, user’s will pay attention longer, will want to learn more, and will be more trusting of your brand.
By instilling trust with storytelling, over 50% of B2B buyers are more likely to consider making a purchase, over 40% are more likely to share that story, and over 15% are more likely to buy a product/service immediately.
So now that we know why brand storytelling is important, let’s take a look at some of our favorite examples of brand storytelling in cybersecurity.
SonicWall
When SonicWall was looking for a cybersecurity marketing firm, they approached Bluetext to help them communicate their unparalleled business values across a variety of industries. Knowing the importance of standing out, Bluetext and SonicWall worked together to create the boundless campaign. The campaign was focused on floating imagery, which served to visualize the liberating feeling of breaking free from cyber threats. The campaign ads depict a series of end users, set in their specific industry. This creates a connection and familiarity with someone within that industry. Imagine seeing someone just like you, in the same industry and roles, facing the same challenges and use cases. This person was liberated from traditional cyber restraints by SonicWall, just as you could be.
To further bring the boundless story to life, Bluetext and SonicWall worked together to promote SonicWall’s Boundless 2020 Virtual event. In the end, this event ended up as the largest virtual event in SonicWall history and drove a 135% increase in attendance over their previous events.
HP
Hewlett Packard’s “The Wolf” campaign is one we often refer to as a masterful example of a company turning a mundane topic into a captivating story. Over the course of this series, Christian Slater infiltrates a company from the mailroom to the boardroom and exposes poorly secured devices on the company’s network. By creating this series with all of the components of a Hollywood box office hit, HP was able to effectively educate users on the importance of device security.
Norton
Another great example of brand storytelling is Norton’s The Most Dangerous Town on the Internet. In short, to quote the film, they visited “some of the most dangerous places on the internet to find out where cybercrime goes to hide.” In the film, the documentarians are able to interview small-time scammers and well-known cybercriminals who’ve infiltrated Google, the US Army, NASA, and more. By creating this documentary, Norton wanted to share an honest look at data havens and the secrets they hide. The authenticity shines through as a refreshing take on cybercrime that not many competitors are willing to share. With over 6 million views on YouTube and awards from Cannes, it’s safe to say this story got the brand’s message across. The story is dark, ghastly, brutally candid, and impossible to forget.

To help create a strong connection with users, as a top brand development agency, we’ve worked with many cybersecurity firms to help them tell their stories in a unique and captivating way. These stories have helped demonstrate that their businesses aren’t just faceless entities; they’re real people working to solve real problems.
Are you interested in working with a top cybersecurity marketing agency to help tell your story? Contact Us!
Thank you for joining us for the Q1 2021 Bluetext Cybersecurity Summit. Exclusively open to CXO’s, our goal with this summit is to deliver a value-add platform to network in the C-Suite with businesses facing similar opportunities and challenges.
Topics:
We plan to discuss the following items:
- Technology Customer Investment Trends
- Technology Consolidation Trends
- 2021 Trends
Date/Time:
2:30pm-4:00pm EST
Thursday, January 28th, 2021
Where:
COMING SOON: A link will be distributed with a calendar invite to all invited.
Agenda:
- Welcome from Jason Siegel: 1 minute
- Welcome and Introduction from Moderator, Morgan Wright, SentinelOne: 3 minutes
- Introductions of each business by one of the representatives (2 minutes each): 15-20 minutes
- Five questions will be softballed out, each receiving 5-10 minutes of airtime.
Summit Specifics: Things to Know
- We will mute all microphones for audio clean-ness
- The raise hand functionality will be used to orderly unmute speakers
- A recording of this conversation will be archived so keep it clean, friends
Moderator
 Morgan Wright
Morgan Wright
Chief Security Advisor, SentinelOne
Morgan is an internationally recognized expert on cybersecurity strategy and cyberterrorism. He currently serves as a Senior Fellow at The Center for Digital Government, Chief Security Advisor for SentinelOne, and is the chief technology analyst for Fox News and Fox Business on cybersecurity, cyberterrorism, national security, and intelligence.
Companies in Attendance:
AffirmLogic
About: AffirmLogic’s Hyperion platform applies advanced Mathematical Behavioral Computation that enables security teams to detect, analyze, and defend against even the most insidious malware—including advanced persistent threats (APTs) and other sophisticated, potentially devastating forms of attack.
Invited:
Larry Roshfeld, Chief Executive Officer
ArdentMC
About: ArdentMC is a trusted provider for geospatial information, cloud migration, and DevOps in the federal, state, and local business spheres, delivering quality products and outstanding performance initiative to every client.
Invited:
Michael Matechak, Chief Strategy Officer
CI Security
About: CI Security provides Managed Detection and Response and Cybersecurity Consulting services to help their customers to be secure, compliant, and resilient against threats to the life-safety, life-sustaining, and quality-of-life systems and services they provide to customers and communities.
Invited:
Jake Milstein, Chief Marketing Officer
EnHalo
About:
EnHalo is a group of global companies under one brand that is locally engaged, while globally operated. EnHalo focuses on three business pillars: Reducing Risk through its cybersecurity offerings, Reducing Cost through digital transformation, and Increasing Revenue through automation.
Invited:
Chris Beard, US President
Carol Watson, Director, Sales & Operations
Illusive Networks
About: Illusive Networks, the leader in deception-based cybersecurity solutions, empowers security teams to preemptively harden their networks against advanced attackers, stop targeted attacks through early detection of lateral movement, and resolve incidents quickly.
Invited:
Claire Trimble, Chief Marketing Officer
Infinite Group (IGI)
About: IGI works with organizations on all levels of IT security. Its areas of practice include managed security, incident response, social engineering, physical & perimeter security, administrative security, and internal security.
Invited:
Andrew Hoyen, President & COO
Kryptowire
About: Kryptowire provides software assurance tools for mobile application developers, analysts, enterprises, and telecommunication carriers.
Invited:
Alex Lisle, Chief Technical Officer
Obrela Security Industries
About: Obrela Security Industries (OSI) provides enterprise-class professional and managed IS services to assess and manage information risk in complex enterprise environments.
Invited:
George Patsis, Chief Executive Officer
Phosphorus Cybersecurity
About: With a 7 year half-life for vulnerability patching, and infrequent, if ever, credential rotation, IoT is the softest target on the network today. Phosphorus automates remediation of the biggest vulnerabilities in IoT.
Invited:
Chris Rouland, Chief Executive Officer
Rebecca Rouland, Chief Financial Officer
Sertainty
About: Sertainty technology implements a proprietary zero-trust architecture by embedding actionable intelligence into data-files. Sertainty makes it possible for data to be self-aware, self-protecting, self-acting. This gives software developers, systems integrators and their end-users a better way to monetize valuable information, lower the cost of compliance and mitigate risk in real time.
Invited:
Rivers Nesler, VP, Communications & Legal Affairs
Securonix
About: Securonix delivers a next generation security analytics and operations management platform for the modern era of big data and advanced cyber threats.
Invited:
German Fabella, Creative Director
SonicWall
About: SonicWall Boundless Cybersecurity safeguards organizations with seamless protection that stops the most evasive cyberattacks across boundless exposure points and increasingly remote, mobile and cloud-enabled workforces.
Invited:
Geoff Blaine, Senior Vice President, Corporate Marketing
SpyCloud
About: SpyCloud is laser focused on preventing online fraud with our proactive solutions, which protect billions of employee and consumer accounts worldwide from account takeover.
Invited:
Company CXO’s
Stage2Security
About: Stage 2 Security is an Adversary Simulation, Protection, and Prevention company focused on building confidence in our clients’ IT systems.
Invited:
George McKenzie, Chief Executive Officer