Winning government cybersecurity contracts is no small feat. With the rise of cyber threats targeting national security, public infrastructure, and sensitive data, government agencies are actively seeking private-sector partners to bolster their defenses. However, for cybersecurity firms targeting business-to-government (B2G) opportunities, standing out in a crowded field requires more than just cutting-edge technology—it demands a strategic approach to marketing. This guide explores the essentials of marketing for cybersecurity firms aiming to secure government contracts, with a focus on compliance, communication, and effective messaging.
Understanding the Regulatory Landscape
Compliance is the foundation of marketing for government cybersecurity contracts. Federal, state, and local agencies operate within strict regulatory frameworks, including standards like:
- NIST Cybersecurity Framework: A cornerstone for ensuring secure systems and processes.
- FedRAMP Certification: For firms offering cloud services to government agencies.
- DFARS Compliance: Relevant for working with the Department of Defense.
Your marketing materials and messaging must demonstrate your firm’s ability to meet these requirements. Incorporate proof of certifications, audits, and adherence to these standards into your website, collateral, and presentations. Without a clear focus on compliance, your firm may fail to even qualify for consideration. Additionally, staying up-to-date with evolving regulations is crucial. As standards and requirements shift to address new threats, your firm’s ability to adapt and demonstrate continued compliance can give you a competitive edge. Regularly review updates to government policies and incorporate those changes into your marketing narrative to showcase your proactive approach.
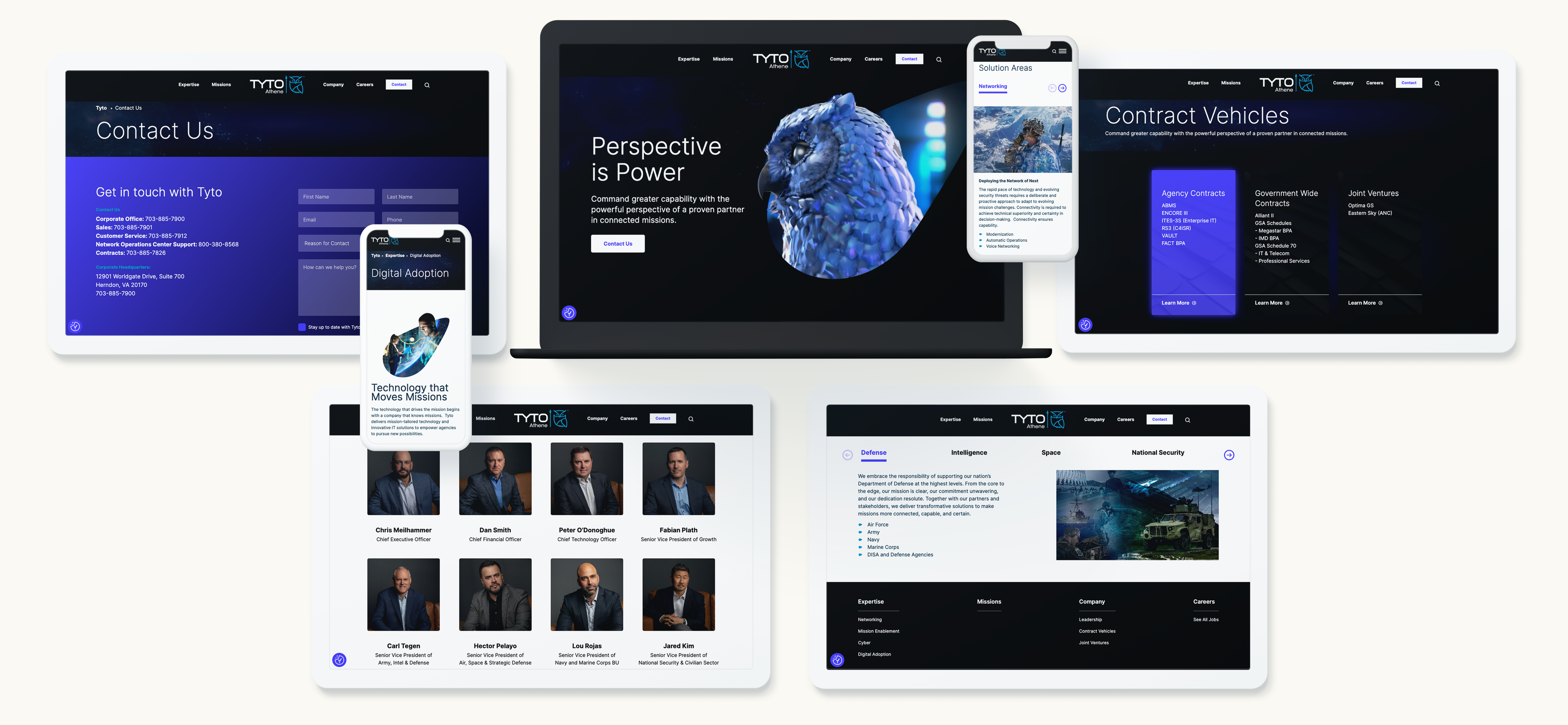
Building Credibility Through Communication
Government agencies are highly risk-averse, especially when it comes to cybersecurity. Establishing trust is key, and the way you communicate can make or break your credibility. Case studies and testimonials play a critical role in this process. Showcase success stories where your cybersecurity solutions have effectively mitigated risks or safeguarded assets. Be specific about measurable results, such as the percentage reduction in breaches or downtime avoided. Thought leadership content is another valuable tool. Publish blogs, whitepapers, and webinars on topics like emerging cyber threats or best practices for securing government systems. Positioning your firm as an industry authority builds trust with decision-makers and reinforces your expertise. Tailored outreach is equally essential. Avoid generic pitches. Research the specific needs and challenges of the agency you’re targeting and craft customized proposals. Personalization signals your genuine understanding of their mission and pain points, which can significantly improve your chances of securing contracts. Consistency across your communication channels ensures your message resonates and reinforces your firm’s expertise. Whether through email campaigns, presentations, or in-person meetings, maintaining a cohesive narrative builds confidence in your capabilities.
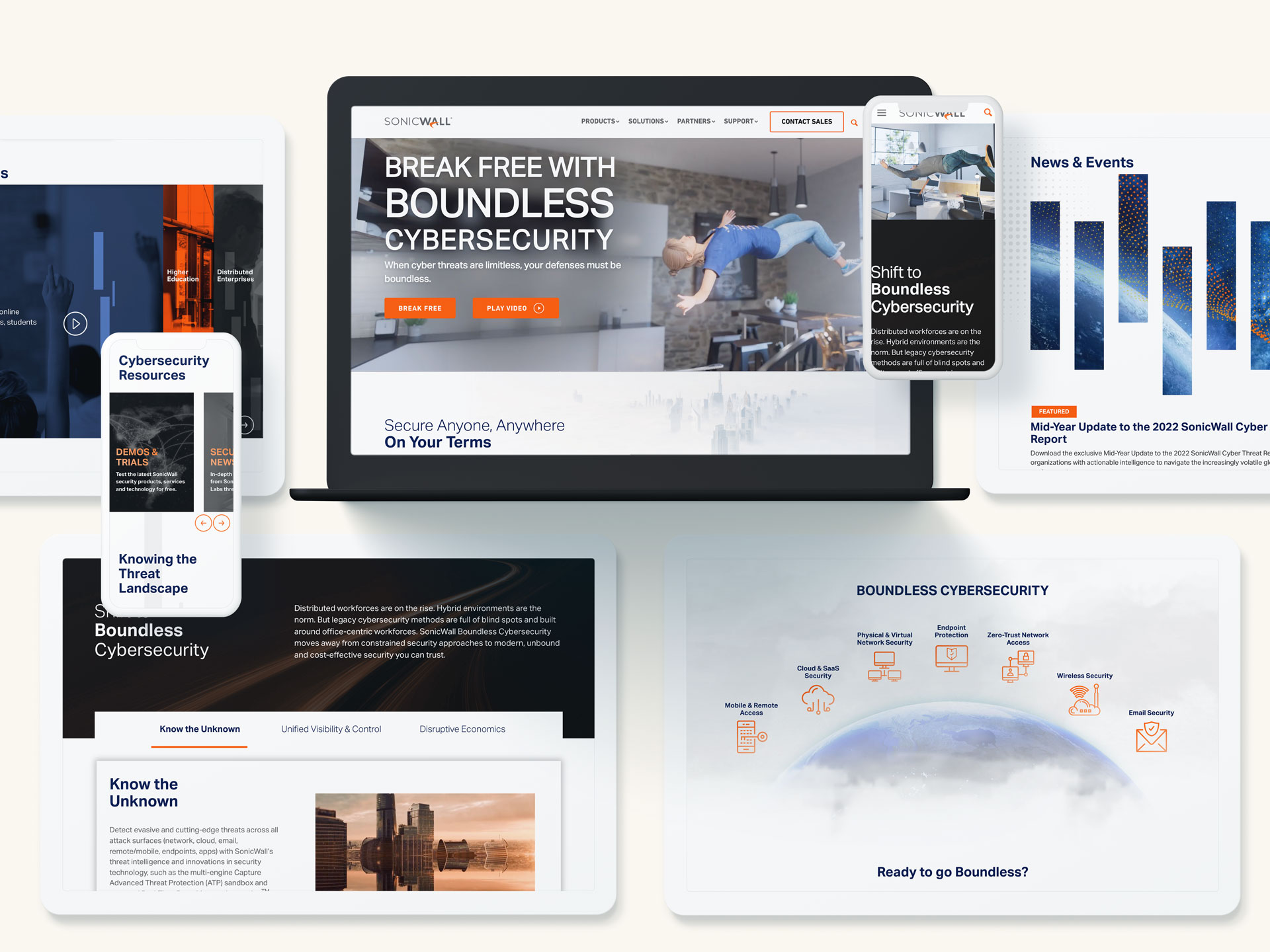
Crafting Resonant Messaging
Government buyers prioritize solutions that align with their mission and address their pain points. To craft effective messaging, emphasize security and resilience. Highlight how your solutions proactively mitigate risks and enhance operational resilience. Speak their language by using terminology familiar to government stakeholders, such as references to “mission-critical systems” or “continuity of operations.” Address cost-efficiency, as budget constraints are a reality for many government agencies. Demonstrate the value and return on investment your firm can provide. Showcase agility by emphasizing how your solutions adapt to emerging challenges. With cyber threats evolving rapidly, government agencies need partners who can keep pace. Your messaging should balance technical depth with accessibility, ensuring both technical evaluators and non-technical decision-makers understand your value. Consider creating audience-specific materials to cater to different stakeholders within the procurement process, from IT specialists to program managers and budget officers. By aligning your messaging with their diverse priorities, you can better articulate your value proposition.
Leveraging Digital Channels for B2G Marketing
Digital marketing is just as important in the B2G space as in commercial markets. Leverage these strategies to amplify your reach: LinkedIn campaigns can target federal and state government decision-makers with sponsored content showcasing your expertise. Search engine optimization (SEO) is critical; optimize your website for keywords like “government cybersecurity solutions” and “FedRAMP-certified services.” Account-based marketing (ABM) focuses on individual agencies, tailoring ads and email campaigns to their unique requirements. Remember to keep your digital assets—from landing pages to downloadable content—compliant with accessibility standards like WCAG, which many government buyers expect. Beyond these tactics, consider investing in webinars and virtual events that cater specifically to government audiences. These platforms allow you to demonstrate your expertise, interact directly with decision-makers, and address their questions in real-time. Additionally, monitor analytics from your digital campaigns to continuously refine your approach, ensuring maximum impact and engagement.

A Strategic Approach to Success
Securing government cybersecurity contracts requires a well-rounded marketing strategy that prioritizes compliance, builds trust, and delivers resonant messaging. By understanding the regulatory landscape, communicating effectively, and leveraging digital channels, your firm can stand out as a reliable partner in protecting the nation’s cyber infrastructure. The competition for these contracts is fierce, but with a clear strategy that emphasizes your strengths and aligns with the unique needs of government agencies, your firm can position itself as a trusted partner in the fight against cyber threats. Ready to position your cybersecurity firm for B2G success? Contact Bluetext today to learn how we can help you navigate the complexities of marketing to government agencies.
The cybersecurity market has grown exponentially in recent years, driven by the increasing frequency of data breaches and cyberattacks. As a result, brands are finding it harder than ever to differentiate themselves in an oversaturated market. Standing out requires more than just advanced technology—it calls for a resilient brand that buyers trust, view as innovative, and recognize as a thought leader.
This blog explores actionable strategies to help your cybersecurity brand carve out its space in a crowded market and position itself as the go-to solution for customers seeking protection in an unpredictable digital landscape.
Establish Trust as Your Competitive Edge
In cybersecurity, trust isn’t just an advantage—it’s a requirement. Organizations are placing their most sensitive data and systems in your hands, making trustworthiness a key factor in every purchase decision. Here’s how you can build and communicate trust effectively:
- Highlight Proven Successes: Showcase your track record with detailed case studies. Demonstrate how your solutions mitigated real-world threats, protected sensitive data, or minimized downtime for clients.
- Emphasize Certifications: Industry certifications like ISO 27001, SOC 2, and GDPR compliance are essential trust signals. Feature them prominently across your website, marketing materials, and sales presentations.
- Be Transparent About Security Practices: Transparency builds confidence. Outline your security protocols, ongoing monitoring processes, and response strategies. This openness demonstrates you have nothing to hide and everything to offer.
By consistently reinforcing trust, your brand will earn the confidence of customers navigating an uncertain cybersecurity landscape.

Communicate Innovation as a Practical Benefit
Innovation is often the first promise cybersecurity brands make—but not all brands know how to communicate it effectively. To make innovation resonate, connect your advancements directly to customer outcomes.
- Focus on Real-World Impact: Instead of advertising “next-gen AI” or “cutting-edge machine learning,” explain how these technologies detect previously unseen threats, reduce false positives, or improve response times.
- Simplify Complex Concepts: Use customer-friendly language and engaging formats like explainer videos, infographics, or live demos to illustrate your innovative capabilities.
- Highlight Your Team’s Expertise: Technology alone isn’t enough—customers value the people behind the solutions. Spotlight your engineers, researchers, and cybersecurity professionals to humanize your innovations.
Positioning your brand as an innovator ensures it remains top of mind for customers seeking modern solutions.


Establish Leadership Through Insightful Content
Thought leadership is one of the most powerful tools in the cybersecurity marketer’s toolkit. Customers look to trusted brands for guidance on navigating a rapidly evolving threat landscape. Use your unique expertise to shape industry conversations and position your brand as a leader:
- Host Webinars on Emerging Threats: Partner with industry experts to educate customers about new and evolving cyber risks.
- Publish Research and Whitepapers: Share data-driven insights on trends such as ransomware, phishing, or AI in cybersecurity.
- Engage in Online Discussions: Build your presence on platforms like LinkedIn and Reddit to connect with your audience directly and share valuable insights.
When your brand becomes a trusted source of information, it naturally rises above competitors who merely offer products or services.

Building a Cybersecurity Brand That Lasts
In today’s crowded market, a resilient cybersecurity brand goes beyond selling solutions. It builds relationships rooted in trust, offers innovations that solve real problems, and educates customers through thought leadership. These efforts don’t just help you stand out—they ensure your brand remains relevant as the cybersecurity landscape continues to evolve.
Looking to differentiate your cybersecurity brand and drive meaningful results? Bluetext specializes in crafting strategies that establish trust, showcase innovation, and build thought leadership for industry leaders. Contact us today to learn how we can help you stand out in the cybersecurity space.
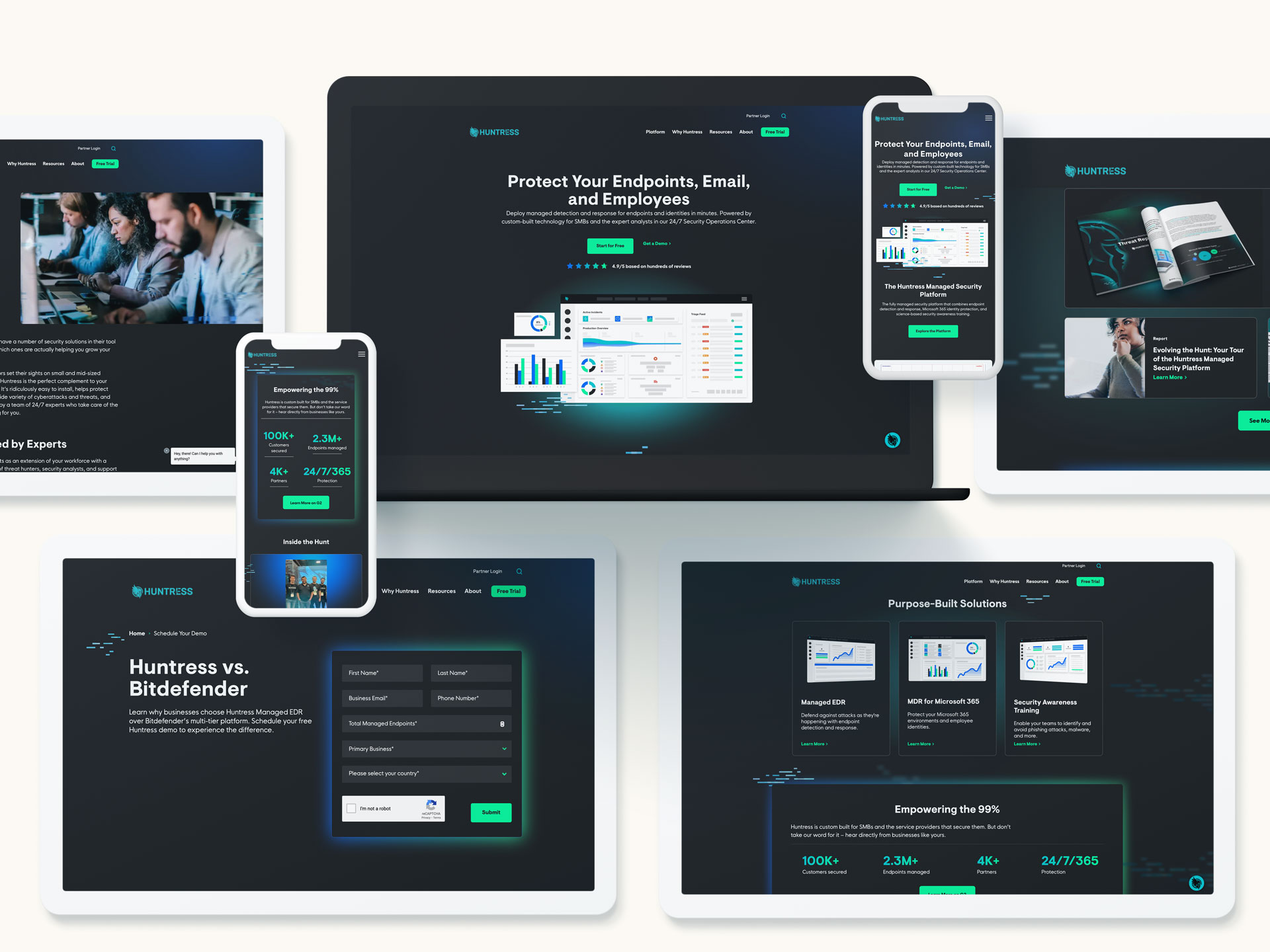
At Bluetext, we’re passionate about empowering cybersecurity companies to thrive in the digital realm. With cyber threats evolving at a rapid pace, it’s essential for these companies to not only provide cutting-edge solutions but also effectively communicate their value propositions to clients. That’s where we come in. Through our innovative approach to cyber security marketing and website design, we help cybersecurity firms of all sizes enhance their digital presence and drive meaningful engagement.
Understanding the Landscape: The Importance of Cybersecurity Marketing
In today’s interconnected world, cybersecurity is no longer just a concern for IT departments—it’s a critical business issue that impacts every aspect of an organization. As cyber threats become more sophisticated, businesses are turning to cybersecurity companies for protection and peace of mind. However, with so many players in the market, standing out can be a challenge. That’s where strategic marketing comes into play.
Cybersecurity marketing is about more than just promoting products and services—it’s about building trust and credibility in an industry where reliability is paramount. At Bluetext, we understand the unique challenges that cybersecurity companies face, from communicating complex technical concepts to reaching the right audience. That’s why we take a holistic approach to cybersecurity marketing, combining creativity, strategy, and technical expertise to deliver results that matter.



Crafting Compelling Digital Experiences: The Role of Website Design
In the digital age, your website is often the first interaction potential clients have with your brand. That’s why it’s crucial to make a lasting impression. At Bluetext, we believe that great design goes beyond aesthetics—it’s about creating meaningful experiences that resonate with your audience and drive action. Our team of experienced designers and developers works closely with cybersecurity companies to create websites that not only look great but also function seamlessly across devices.
From intuitive navigation to engaging content, we ensure that every aspect of your website is optimized to convert visitors into leads. Whether you’re a startup looking to make a splash or an established firm seeking to rebrand, we have the expertise and creativity to bring your vision to life.



Tailored Solutions for Every Need: Our Approach to Cybersecurity Marketing
At Bluetext, we understand that every cybersecurity company is unique. That’s why we take the time to listen and understand your specific goals and challenges. Whether you’re looking to increase brand awareness, generate leads, or improve customer retention, we develop custom marketing strategies tailored to your needs.
From content marketing and social media management to search engine optimization and email campaigns, we offer a full suite of services designed to help you achieve your business objectives. And with our data-driven approach, you can be confident that every decision we make is backed by insights and analytics.

Looking to the Future: Innovation in Cybersecurity Marketing
As technology continues to evolve, so too does the threat landscape. At Bluetext, we’re committed to staying ahead of the curve and helping our clients navigate the ever-changing digital landscape. Whether it’s adopting emerging technologies or exploring new marketing channels, we’re always looking for ways to innovate and drive results for our clients.
Private Equity Firms Investing in Cybersecurity Companies
Private equity firms can learn from Bluetext’s approach to empowering cybersecurity companies in the digital realm. As investors seek opportunities in the cybersecurity sector, understanding the importance of effective marketing and digital presence becomes essential. Bluetext’s holistic approach, combining creativity, strategy, and technical expertise, serves as a valuable model for private equity firms looking to maximize the value of their investments in cybersecurity. By partnering with marketing agencies like Bluetext, private equity firms can ensure that their portfolio companies effectively communicate their value propositions, differentiate themselves in a competitive market, and ultimately drive growth and success in the cybersecurity industry.
In conclusion, cybersecurity companies play a vital role in protecting businesses and individuals from cyber threats. At Bluetext, we’re proud to support these companies by providing strategic marketing and website design services that elevate their digital presence and drive meaningful engagement. With our expertise and passion for innovation, we’re confident that together, we can build a safer, more secure digital future.
Are you ready to take your website to the next level? Contact us.
In today’s digital age, cybersecurity has become an increasingly critical concern for businesses of all sizes. With the constant evolution of cyber threats, staying informed about the latest trends, technologies, and best practices is paramount. Thankfully, the cybersecurity community offers a plethora of events where professionals can gather to share knowledge, network, and explore innovative solutions. In this blog post, we’ll highlight some upcoming cybersecurity events in 2024 that companies should consider attending and provide insights into maximizing brand awareness opportunities through strategic marketing approaches.
Must-Attend Cybersecurity Events in 2024
- RSA Conference
- Date: May 6-9, 2024
Known as one of the largest and most influential cybersecurity events globally, the RSA Conference gathers thousands of cybersecurity professionals, industry experts, and thought leaders under one roof. Attendees can participate in educational sessions, hands-on workshops, and networking events. To sign up for the RSA Conference, visit their official website and register for the event.
- Date: May 6-9, 2024
- Black Hat USA
- Date: August 3-8, 2024
Black Hat USA is a premier event for the cybersecurity community, focusing on the latest in information security research, development, and trends. The conference features briefings, trainings, and a bustling business hall where companies showcase their products and services. Registration for Black Hat USA can be done through their website, offering various pass options to suit different needs.
- Date: August 3-8, 2024
- DEF CON
- Date: August 8-11, 2024
DEF CON is an iconic cybersecurity conference known for its hacker culture and emphasis on hands-on learning. It features diverse content ranging from cutting-edge research to cybersecurity challenges and competitions. Companies looking to engage with the hacker community and showcase their expertise can explore sponsorship opportunities available on DEF CON’s website.
- Date: August 8-11, 2024
- Cyber Security Summit Series
- Date: Various dates and locations throughout 2024
The Cyber Security Summit Series hosts events across major cities, providing a platform for cybersecurity professionals to discuss emerging threats and solutions. These regional summits offer valuable networking opportunities and practical insights tailored to local cybersecurity landscapes. Interested companies can find event details and registration information on the Cyber Security Summit Series website.
- Date: Various dates and locations throughout 2024
Maximizing Brand Awareness Opportunities
Attending cybersecurity events presents an excellent opportunity for companies to enhance their brand awareness and establish thought leadership within the industry. Here are some strategies to consider:
- Sponsorship and Exhibiting: Investing in sponsorship packages or setting up exhibition booths can significantly amplify brand visibility. Companies can customize their presence with branded materials, demos, and interactive experiences to engage attendees.
- Speaking Engagements: Securing speaking opportunities allows companies to showcase their expertise and insights to a captive audience. Whether through keynote presentations, panel discussions, or technical talks, speaking engagements can position individuals as thought leaders and elevate brand credibility.
- Networking and Relationship Building: Encourage team members to actively network with attendees, industry peers, and potential clients. Meaningful interactions can lead to valuable partnerships, collaborations, and business opportunities down the line.
- Content Marketing: Leverage event participation to generate valuable content such as blog posts, whitepapers, or video recaps. Sharing key takeaways, trends, and insights from the event demonstrates thought leadership and keeps the audience engaged beyond the conference.
- Social Media Engagement: Utilize social media platforms to amplify event presence before, during, and after the conference. Live tweeting, posting photos, and sharing updates can extend reach, foster engagement, and drive traffic to company profiles and websites.
In conclusion, cybersecurity events offer a wealth of opportunities for companies to stay abreast of industry developments, connect with peers, and showcase their brand. By strategically planning participation and leveraging various marketing tactics, businesses can maximize their presence, foster meaningful connections, and solidify their position as leaders in the ever-evolving cybersecurity landscape.
Looking to maximize your attendance at any of this year’s events? Contact us to learn how we can help.
Understanding the Importance of Data Privacy and Security
In today’s interconnected world, data has become one of the most valuable assets for businesses. However, with great power comes great responsibility. Consumers are more vigilant than ever before about how their personal information is collected, stored, and utilized by companies. Data breaches and privacy scandals have eroded trust in brands, highlighting the critical need for transparency and accountability in data handling practices.
Transparency Builds Trust
Transparency is key to building trust with consumers. Brands should clearly communicate their data collection practices, the purposes for which data is used, and the measures taken to protect it. This transparency fosters a sense of control and empowerment among consumers, reassuring them that their information is being handled responsibly.
Compliance with Regulations
Regulations such as the General Data Protection Regulation (GDPR) and the California Consumer Privacy Act (CCPA) have raised the bar for data privacy standards and accountability. Compliance with these regulations is not only a legal requirement but also a demonstration of a brand’s commitment to respecting consumers’ rights. Marketers must ensure that their data collection and processing practices align with the requirements of relevant regulations to avoid fines and reputational damage.
Prioritizing Consumer Consent
Obtaining explicit consent from consumers before collecting their personal data is crucial for maintaining trust and compliance with regulations. Marketers should provide clear and easily understandable consent forms that outline the purposes for which data will be used and offer options for consumers to opt out if they so choose. Respecting consumers’ choices and preferences demonstrates a commitment to ethical data handling practices.
Securing Data Against Cyber Threats
In addition to regulatory compliance and transparency, brands must invest in robust cybersecurity measures to protect against data breaches and cyber threats. This includes encryption, access controls, regular security audits, and employee training on data security best practices. By safeguarding data against unauthorized access and misuse, brands can instill confidence in consumers and mitigate the risks associated with data breaches.
Data Security From a Private Equity Perspective
From a private equity perspective, the significance of data privacy and security in digital marketing cannot be overstated. As investors assess potential targets or portfolio companies, they increasingly scrutinize data handling practices as a critical aspect of risk management and value creation. Brands that prioritize transparency, compliance, and trust not only mitigate regulatory and reputational risks but also enhance their attractiveness to investors. Private equity firms recognize that robust data privacy and security measures not only safeguard consumer trust but also contribute to the long-term viability and value of their investments. By aligning with regulatory requirements, obtaining explicit consumer consent, and implementing stringent cybersecurity protocols, companies can demonstrate their commitment to responsible data management practices, ultimately bolstering their appeal to investors and stakeholders alike.
Conclusion
In an era defined by data-driven marketing, prioritizing data privacy and security is no longer optional—it’s a business imperative. By prioritizing transparency, compliance with regulations, obtaining consumer consent, and implementing robust cybersecurity measures, marketers can build trust with their audience and differentiate themselves in a crowded marketplace. Embrace data privacy and security as core pillars of your digital marketing strategy and pave the way for long-term success in the digital age. Contact us to learn more.
In a world where the digital battleground is ever-evolving, the way we visualize cyber threats is more than just a matter of aesthetics. It’s about conveying a message that resonates with the complexity and urgency of the challenges we face. Over the years, cybersecurity branding has gone through various phases, from the ominous figures in dark hoodies to monstrous depictions of malware. But now, a new trend is emerging—one that’s straight out of a science fiction saga.
The Evolution of Cyber Security Symbolism:
Let’s take a quick trip down memory lane to understand how cybersecurity brands have evolved in their visual language:
- The Hooded Figures: Once upon a time, cybersecurity brands leaned heavily on the stereotype of hackers as mysterious figures cloaked in darkness, lurking in the shadows of the digital realm. While this imagery effectively conveyed the sense of a hidden threat, it also perpetuated stereotypes and failed to capture the true nature of cyber adversaries.


- Abstract Digital Art: In this phase, cybersecurity brands leaned towards abstract digital art to represent cyber threats. They utilized geometric shapes, neon colors, and glitch effects to convey the complexity and unpredictability of digital vulnerabilities. While visually captivating, this approach sometimes lacked a clear connection to the real-world implications of cyber attacks.


- Monstrous Malware: As the threat landscape expanded, so did the imagery associated with cyber threats. Brands began depicting malware as monstrous creatures, embodying the destructive potential of cyber attacks. While this approach added a layer of visual interest, it often bordered on the cartoonish and failed to convey the sophistication of modern cyber threats.


But now, a new era has dawned in the world of cybersecurity branding—one that draws inspiration from the boundless realms of science fiction. Enter the age of Sci-Fi Inspired Branding.
Incorporating elements from the vast expanse of the cosmos, cybersecurity brands are embracing a visual language that speaks to the futuristic nature of the challenges we face. Here are some examples of websites that are boldly venturing into this new frontier:
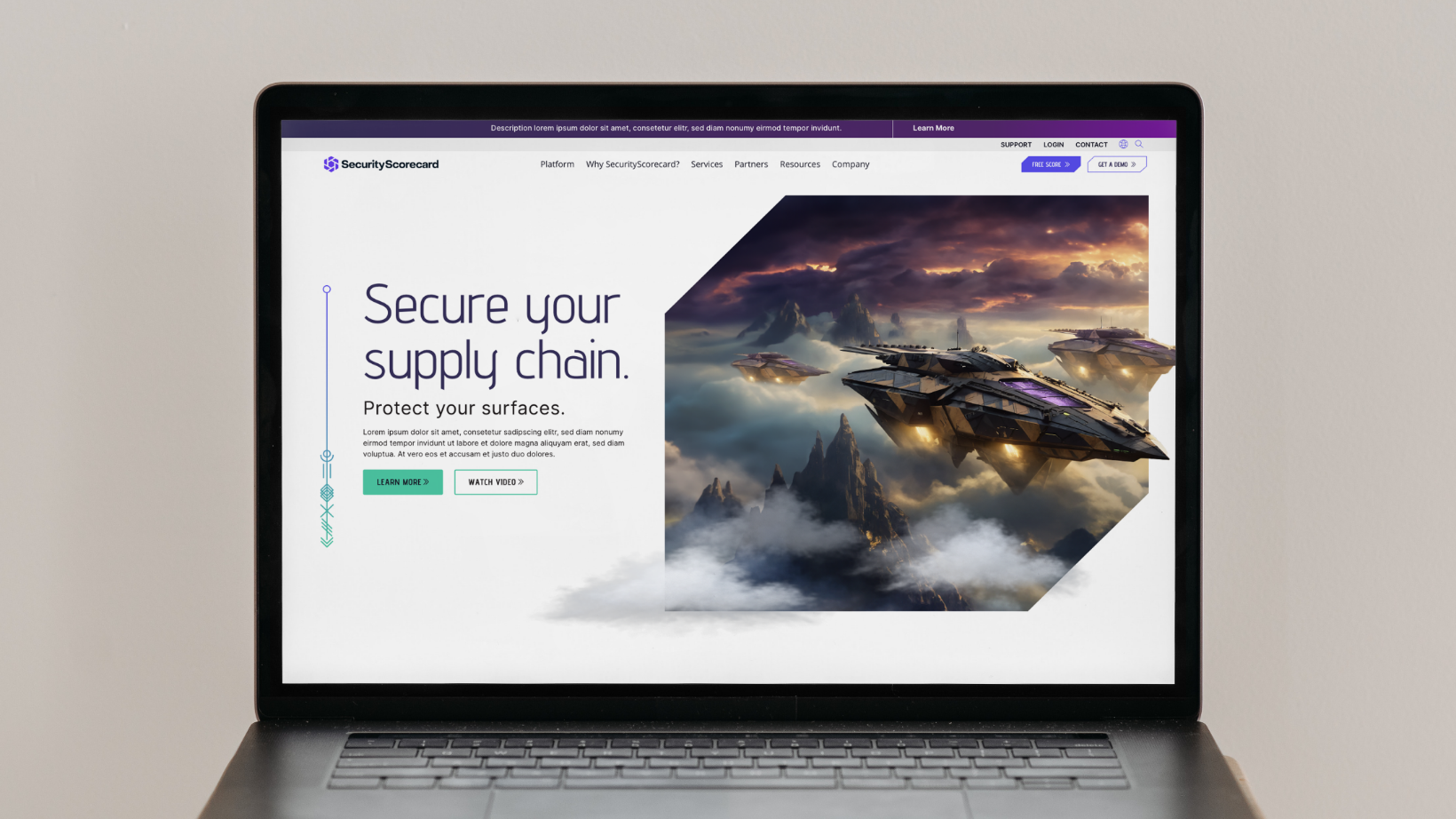
- SecurityScorecard: With its sleek interface and futuristic aesthetic, SecurityScorecard’s website feels like something straight out of a cyber-thriller video gam. The use of dynamic visuals and futuristic typography conveys a sense of innovation and technological prowess. Check out how Bluetext contributed to this brand revolution.
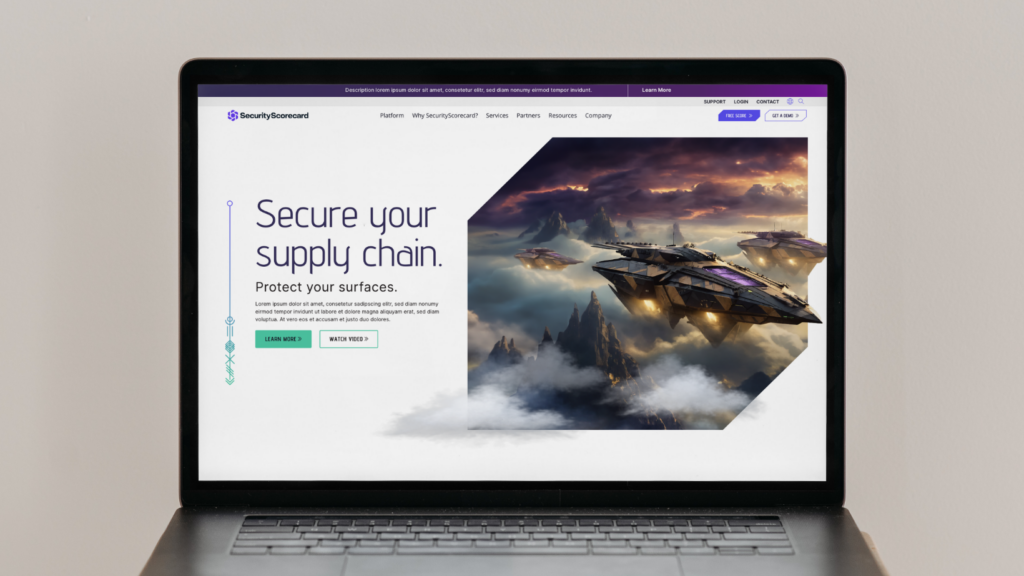



- Cybereason: Cybereason’s website takes visitors on a journey through the digital universe, with swirling nebulae and sleek spacecraft serving as the backdrop for its cybersecurity solutions. The use of space-themed imagery reinforces the brand’s message of protecting against unknown threats from the far reaches of the digital universe.


- CrowdStrike: As you scroll through CrowdStrike’s website, you’re greeted with a cast of characters straight out of a sci-fi epic—space cowboys and invaders battling it out against a backdrop of cosmic chaos. This playful yet powerful imagery captures the essence of the cyber threat landscape while injecting a sense of adventure into the brand’s messaging.




- Darktrace: Darktrace’s website transports visitors to a futuristic landscape filled with shimmering data streams and pulsating energy fields. The use of sleek, metallic textures and holographic interfaces creates an immersive experience that reflects the cutting-edge nature of the company’s AI-driven cybersecurity solutions.


- SentinelOne: SentinelOne’s website features sleek spacecraft navigating through asteroid fields and alien landscapes. The use of dynamic animations and sci-fi-inspired imagery reinforces the brand’s message of protecting against next-generation cyber threats.


- Varonis: Varonis’ website features sleek, robotic figures that rise against a futuristic backdrop. The use of sci-fi-inspired visuals and dynamic animations creates a sense of immersion, highlighting the company’s innovative approach to data security and threat detection. Varonis’ website captures the imagination and reinforces the brand’s message of protecting against cyber threats in the digital age.


As the line between science fiction and reality is becoming increasingly blurred, it’s only fitting that cybersecurity brands embrace the boundless possibilities of the sci-fi universe. By infusing their visual identity with elements from the farthest reaches of space, these brands are not only staying ahead of the curve but also inspiring a sense of wonder and imagination in their audiences.
So, the next time you find yourself navigating the digital wilderness, remember that the guardians of cyberspace are not just warriors—they’re spacefaring adventurers on a mission to protect the frontiers of the digital realm.
The cybersecurity market is ever-evolving, and with it, digital marketing strategies should anticipate these trends and adapt to stay ahead of them. Careful market analysis and years of industry expertise amongst Bluetext marketing specialists reveal AI technology, increased investment from SMBs, and enterprise risk quantification are expected to impact cybersecurity provider marketing strategies in 2024.
Cybersecurity Trends to Watch:
Artificial Intelligence is Impacting All Industries — Including Cybersecurity
We’ve seen AI headlines not just in the Tech markets, but all over the mainstream media. As utilization of AI becomes more prevalent, with access to open-source models like ChatGPT, cybersecurity providers will need to develop entirely new standards of trust. Organizations will be seeking cybersecurity providers to ensure they can securely deploy AI technology. On top of that, malicious uses for AI will increase the need for protection against cyber attacks. Cybersecurity providers will need to speak to their ability to deploy safe AI product features while also promoting their ability to protect against these AI-powered attacks.
Check out how Bluetext client AmeliaAI leverages conversational AI as a tool for business optimization.


SMB Organizations are Investing More in Cybersecurity
Managed services are becoming an increasingly important purchase for small and medium-sized businesses. Security attacks on SMBs are felt deeply throughout the organization, compared to large enterprises that may find more protection in silos and sheer size. The good news is that, because of increased awareness of this vulnerability, SMBs’ spending on cyber security is expected to reach $109 billion worldwide in 2026. Cybersecurity providers should take advantage of this growing customer base and make additional considerations for SMB target audiences when designing digital marketing strategies.
Enterprises Are Seeking Better Quantification of their Cybersecurity Risks
For enterprise decision-makers, their willingness to invest in cybersecurity measures will hinge on the ability to accurately quantify their current risks. According to Gartner, turnover in the CISO position is an increasing threat to enterprises; they expect 50% of cybersecurity leaders will have left their positions by 2025. A large contributor to CISO stress is a lack of organizational support for seeing cybersecurity measures as a crucial element of meeting business objectives. Calculating the degree of security risk at an enterprise will play a key role in getting organizational buy-in for increased cybersecurity measures. Marketing strategies will need to speak to both cybersecurity leaders (who are looking to fortify their security measures) and executives (who are looking to advance business goals).
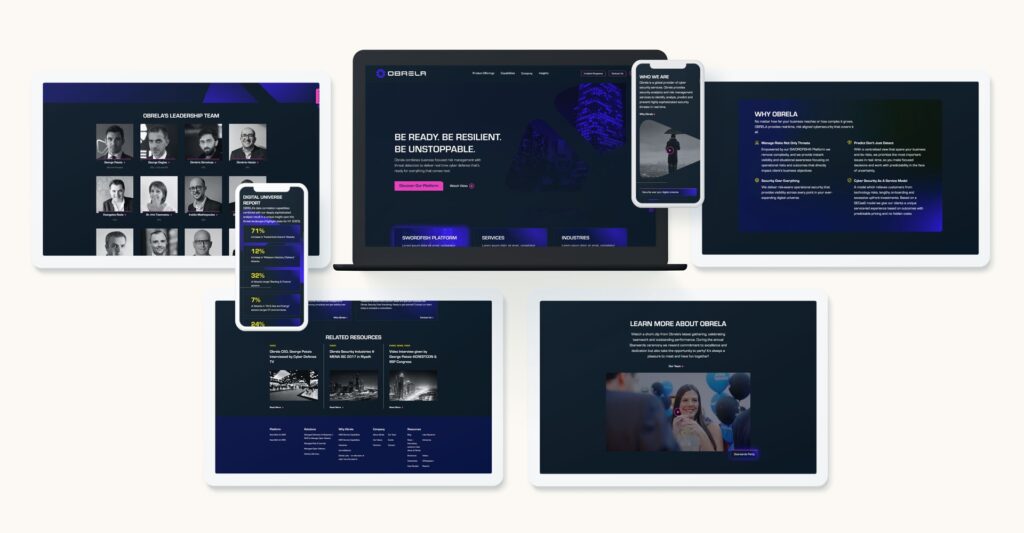
Check out our recent work with Obrela, a world-class cyber security provider, who came to Bluetext for support in updated brand, logo, messaging, website, and video to connect with technical and executive-level audiences.

A digital marketing agency can help your company stay on top of the latest trends in cybersecurity and figure out a plan for how to address these trends in your overall marketing strategy. At Bluetext, we specialize in working with industry-leading cybersecurity professionals; see how we work with companies to build credibility in the realm of cybersecurity in this recent blog.
Curious about what other trends we expect to see in the upcoming year? Read our blog on the 2024 Future Forecast from Bluetext.
In the competitive world of cybersecurity, standing out in search engine results is crucial. However, achieving high rankings requires a unique approach tailored to the industry’s nuances. In this blog post, we’ll explore SEO strategies specifically designed for cybersecurity brands.
1. Secure and Mobile-Friendly Websites
Search engines prioritize secure and mobile-friendly websites. Ensure that your site is HTTPS secured, providing a safe browsing experience. Mobile responsiveness is also a crucial factor, considering the increasing use of smartphones for online activities.
When designing new websites for our clients, we subscribe to a mobile-first mentality, ensuring any new website design works seamlessly on mobile devices. Take our work with Securonix for example. Securonix delivers a next-generation security analytics and operation platform for the modern era of big data and cyber threats. They came to Bluetext to evolve their brand and website with a completely new look. One of the major components of the rebuild of the Securonix website was to ensure every part of the website looked and worked seamlessly on various mobile devices across multiple browsers. Bluetext did extensive regression and cross-browser testing to ensure all pages and functionality were rendered and functioned as intended.

2. Targeted Keyword Optimization
Identify and optimize for relevant keywords specific to cybersecurity. Tailor your content to address common queries and concerns in the cybersecurity landscape. Long-tail keywords that reflect user intent can be particularly effective in attracting the right audience.
A key deliverable in any Bluetext website design and development engagement is the creation of an SEO roadmap, identifying keywords to be implemented across the website including headlines, blog posts, and navigation menus.
3. Quality Content with Expertise
Create high-quality, authoritative content that showcases your expertise in cybersecurity. This can include in-depth articles, whitepapers, and case studies. Valuable content not only attracts organic traffic but also positions your brand as a trusted source of information.
When developing a new website for our clients, we always recommend developing a robust blog program to establish brand credibility and increase SEO on-page ranking. If clients don’t have the resources in-house to create blog content, we’re happy to do so on their behalf as part of our engagement, ensuring the utilization of the correct SEO keywords and topics.
4. Technical SEO Best Practices
Implement technical SEO best practices, such as optimizing meta tags, improving website speed, and enhancing site navigation. Search engines reward websites that provide a smooth and user-friendly experience.
One tool you can utilize is Google’s PageSpeed Insights. You can analyze your existing website and determine ways to improve your technical SEO score, boosting your on-page search results.

5. Backlinks from Trustworthy Sources
Build a strong backlink profile by obtaining links from authoritative and trustworthy sources within the cybersecurity domain. Collaborate with industry influencers, participate in cybersecurity forums, and contribute to reputable publications to earn quality backlinks.
6. Regular Security Audits
Perform regular security audits not only for the safety of your users but also for SEO. Search engines may penalize insecure websites. By maintaining a secure online environment, you not only protect your users but also ensure your site’s visibility in search results.
7. Local SEO for Targeted Reach
If your cybersecurity brand operates in specific regions, leverage local SEO strategies. Optimize your Google My Business profile, include location-specific keywords, and participate in local cybersecurity events to enhance your presence in local search results.
By combining these SEO strategies tailored for cybersecurity, you can not only improve your search engine rankings but also establish your brand as a go-to resource for users seeking reliable and secure solutions in the digital realm. Need support in developing your SEO strategy? Contact Bluetext for help.
Influencer marketing is a buzzword across industries, but how does it fare in the realm of cybersecurity? In this blog post, we’ll delve into the potential and challenges of influencer marketing for cybersecurity brands.
1. Identifying the Right Influencers
In the cybersecurity space, authenticity is key. Look for influencers who not only have a substantial following but also possess genuine expertise in the field. A cybersecurity influencer should be able to speak knowledgeably about your product and its benefits.
2. Educational Collaborations
Collaborate with influencers on educational content. Webinars, live sessions, or joint blog posts that provide valuable insights into cybersecurity trends and solutions can be mutually beneficial. This not only promotes your brand but also enhances the influencer’s credibility; a win-win situation for both parties.
3. Authentic Endorsements
In the world of cybersecurity, trust is paramount. Ensure that influencers authentically endorse your product based on its merits. Genuine recommendations resonate more with the audience and contribute to building trust in your brand as well as the authenticity of the influencer.
4. Thought Leadership Partnerships
Align your brand with influencers who are considered thought leaders in cybersecurity. Their endorsement not only boosts your credibility but also positions your product as a cutting-edge solution in the eyes of your target audience.
5. Addressing Trust Concerns
Be mindful of potential trust issues that may arise. Clearly communicate any influencer partnerships to your audience, emphasizing the shared values and commitment to cybersecurity. Transparency is crucial in maintaining the trust you’ve worked hard to build.
6. Metrics and Measurement
Define clear metrics to measure the success of influencer collaborations. Whether it’s increased website traffic, engagement on social media, or conversions, having quantifiable goals ensures that your influencer marketing efforts align with overall business objectives.
Influencer marketing in cybersecurity can be a powerful strategy if approached with authenticity and strategic thinking. By choosing the right influencers and maintaining transparency, you can leverage their reach to enhance your brand’s credibility and reach a wider audience.
Interested in learning more about the power of influencer marketing and how it can impact your marketing strategy? Contact us here at Bluetext.
Social media isn’t just for sharing cat videos and memes; it’s a powerful tool for cybersecurity marketing. In this blog post, we’ll explore how marketers can leverage social media platforms to promote cybersecurity solutions effectively.
1. Educational Content
Use social media to share bite-sized, educational content about cybersecurity threats and best practices. Infographics, short videos, and quick tips engage your audience and position your brand as an informative resource. Short-form content is also easily digestible for your audience and can be shared easily across multiple social platforms with relative ease.
2. Interactive Webinars and Live Sessions
Host live webinars or Q&A sessions on platforms like Facebook or Instagram. This not only provides valuable information to your audience but also allows for direct interaction, building a personal connection between your brand and potential customers.
3. Cybersecurity Challenges and Quizzes
Create interactive challenges or quizzes related to cybersecurity on platforms like X or Instagram. Engaging content not only attracts attention but also educates your audience in a fun and memorable way.
4. Highlight Security Features
Use platforms like YouTube to create video content showcasing the security features of your products. Seeing is believing, and visual demonstrations can be powerful in conveying the effectiveness of your cybersecurity solutions.
Check out this product essence video we created for cybersecurity startup, Phosphorus, bringing their product to life in a creative yet informative way.
5. Partner with Influencers
Collaborate with influencers in the cybersecurity space to amplify your reach. Influencers can provide authentic endorsements and reach audiences that may be otherwise challenging to access through traditional marketing channels.
By strategically utilizing social media, cybersecurity marketers can connect with their audience, educate them about the importance of security, and establish a strong online presence. To learn more about developing a captivating social media strategy in the cybersecurity industry, contact us.