Spider Chart, Spider Chart,
Visualizes whatever a spider can
Spins a chart, any size,
Catches insights just like flies
Look Out!
Here comes the Spider Chart
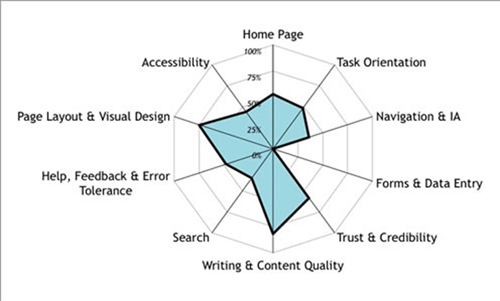
A spider chart plots the values of each category along a separate axis that starts in the center of the chart and ends on the outer ring. These charts are great ways of visualizing the strengths and weaknesses of your current or future state website user experience. At Bluetext we have a deep focus on the science of user experience. After all, when you design and build sites for Fortune 500 companies, every fraction of a percent counts.
Bluetext likes to help visualize the various states of our analysis in spider graphs.
Competitive Analysis Visualization Through Spider Graphs
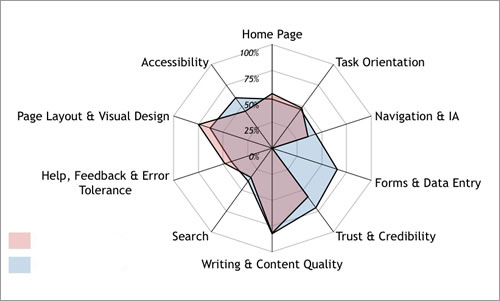
In today’s fast moving digital marketing world it’s critical to be a watchful eye for our clients to ensure they have a competitive advantage. A real time pulse and visualization of where they fall in the competitive marketplace can be very valuable. The below sample spidergraph can show a marketing leader where they stack in many categories. They can review these sequentially chronologically to see how they are progressing and ensure they have the best opportunity to capture and convert users across their desired journeys to achieve the key performance indicators the site is measured against.
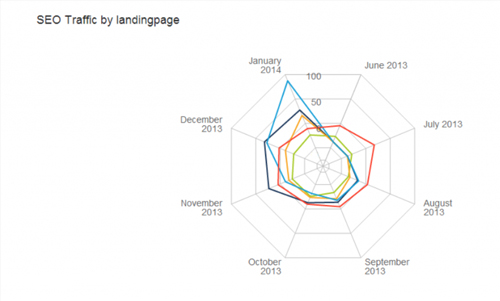
SEO and Landing Page Optimization Visualization Through Spider Graphs
If you really want to impress during a presentation, this is the chart for you. It allows you to display multivariate data easily while also impressing with the visual appeal of its radar shape. Check out the chart above which shows SEO traffic by landing page. This Spider Chart stylishly displays SEO traffic for each series of pages in a specific time frame. This kind chart allows you to easily see real SEO traffic rather than just keyword ranking reports like those from Google Analytics. At the end of the day, the quality and amount of traffic matters more than just keyword ranking. translations The Spider Chart can be used to hold the attention of your audience as you explain the insights you’ve discovered in a way which won’t scare them off.
These charts are just the tip of the data visualization iceberg. Talk to us at Bluetext about your story, brand, or data visualization needs.
Brand Strategy. Brand Presentation. Brand Delivery. Bluetext.
Ok all you Thornton Mellon fanatics, the stats are in and the truth must be told. Some interesting data points I hope you all reflect on as you gear up for going back to school.
DATA POINT NUMBER ONE – DEDICATED TO OUR FAVORITE TEACHER SAM KINISON
The mobile revolution is complete. Smartphones account for more than half of searches in 10 countries—including the U.S. and Japan—according to Google, which didn’t release exact percentages or a full list of countries.
Why this is important?
Is every aspect of your digital infrastructure optimized for mobile?
You shouldn’t just stack your desktop elements. You should think through the human factors of mobile design and what your users truly want in the palm of their hand on first visit. Mobile first should be in the DNA of your marketing organization.
DATA POINT NUMBER TWO: THE TRIPLE LINDY OF DATA POINTS
60% of B2B marketers use web traffic to measure success instead of using sales lead quality or social media sharing.
Why this is important?
Success comes down to the key performance indicator and the analytics that you can generate. It’s much easier to track performance and measure return on investment with reliable website traffic data. Great data gives you a clear picture of an online campaign’s viability, but traffic isn’t your only solution. This stat also shows the immaturity of marketing measurement in the majority of organizations and the need for more in-depth data and analysis. If you can ramp up your content marketing analytics in 2015, you’ll be leaps ahead of your competitors.
DATA POINT NUMBER THREE: EMAIL GETS NO RESPECT
63% of consumers prefer to be contacted by email
A new study by Adobe claims that marketers are failing to engage ‘email addicts.’
While 63% say they prefer to be contacted by email, only 20% favor direct mail, 6% social media, 5% the brand’s mobile app, 4% text message and 2% phone.
Why this is important?
Surprisingly, this shows that email campaigns are favored way above even the second most-preferred form of contact from brands, suggesting that email marketing should still be high on every digital marketer’s agenda.
In the crowded and highly-competitive government market, how do you differentiate your brand from your competitors?
While you’re thinking about how to stand out from the crowd, download a poster from our Adult Coloring Book that you can bring to life, and let Bluetext solve your bigger marketing challenges.
Click here to download our free Adult Coloring Book!
Last week some very interesting data came out of Parse.ly, an analytics firm which collects data for 400 digital publishers including Conde Nast, Reuters, Mashable, and The Atlantic. The headline is that, as of June 2015, Facebook is driving more traffic to websites than Google’s sites including google.com and Google News.
HUH you ask? How is that possible? Google is the king of referral traffic, right? It is all about search engine optimization.
Not so fast. The data points to some recent shifts in how Facebook focuses on driving content to its site, and validates the fact that this is not some random stat that will course correct. The trend line has actually been going this way since 2012.
So as a marketer, what are you to do? Well, don’t ring the alarm bells too quickly. Search engine optimization is still critical for success and needs to be a big part of your marketing mix. But don’t ignore Facebook and write it off as a nice place for consumers to share pictures with friends. That is an uneducated and naïve viewpoint and one that is clearly not valid based on these numbers.
I think it is safe to say that Facebook is just getting started, and optimizing your content to play off the Facebook algorithms, as much as that is possible, is a very smart approach. Some of the concepts that we continuously share with clients include:
- Make your Content snackable and consumable
- Encourage social sharing
- Create conversation and dialogue
- Be unique, relevant, or different, but never be boring
How is your organization optimizing social content? Are you seeing an uptick in conversations due to your efforts or are you just scratching the surface?
Bluetext was one of the first agencies to sound the alarm for mobile-optimized websites after Google tweaked its search algorithm in late April. Dubbed “MobileGeddon” by SEO experts, Google announced that it would now reward mobile-friendly sites in search results that were coming from mobile devices. The only question in the minds of search marketers was how much of an impact this would have, or whether it was more of a bluff.
The results are in, and this was no bluff! According to a survey by Moovweb, having a mobile-friendly site is absolutely essential in the SEO competition for search result rankings. Moovweb tracked more than 1000 important keywords across a range of industries over a six-week period to see if Google was serious. Here is a snapshot of the results:
• 83 percent of the key words returned a mobile-friendly website as the top result.
• In 81 percent of the cases, the top three rankings went to mobile-friendly sites.
• When looking at all 10 of the search results that make up the first page of a Google search, 77 percent were mobile-friendly.
In other words, if you aren’t mobile-optimized, the odds of landing towards the top of a search, or even at the bottom of the first page, are very low. And for any company that relies on search to drive leads, conversions or outright sales, that can be very costly. According to recent report on CNN Money, the fall from the top can be precipitous:
• The top spot on a search result receives 20-to-30 percent of the page’s clicks;
• Spots number two and three produce five-to-10 percent of the page’s clicks;
• Any results below the fold attract less than one percent of the clicks;
• If you’re on the second page or lower, your clicks from search will be negligible.
The survey results can be interpreted as the glass being half full and as the glass being half empty. It’s impressive that such a high percentage of results returned mobile-friendly sites, demonstrating that companies with a lot at stake were able to quickly meet the Google requirements. That might be partly explained by Google’s early warning to the market that it was making this change—a heads up that Google has rarely given previously when it comes to search algorithm revisions.
On the other hand, who are the companies that show up in the 17 percent of the top results where sites are not mobile-friendly? The survey doesn’t say, but those brands may not be there for long. As the impact of the algorithm changes continues to be felt, those numbers will all climb towards 100 percent.
What’s interesting about the results when broken down by industry is that some sectors are more advanced than others, at least based on this survey. For example, retail has the highest percentage of mobile-friendly sites ranked in the number one spot for the keywords that Moovweb reviewed. That makes sense, as retailers have been early adapters in the mobile commerce world where the competitive stakes are so high. Close behind are healthcare, insurance and travel and hospitality.
Lagging far behind are the education and transportation verticals. These markets may simply not be as competitive in terms of SEO and are behind on the “mobile maturity” curve. Yet, as the use of mobile devices increases and search engine results become more important and more competitive in these lagging markets, organizations without a mobile-optimized platform will be left behind.
Here’s the bottom line: MobileGeddon is real, and the effects are being seen as well as felt. Even small changes to Google’s search engine algorithm can have a huge impact on a brand. The CNN Money report cites one company that had to lay off 10 percent of its work force because of its slide down the search result pages. Mobile matters, and that will only become more apparent over time.
If Jon Favreau’s character in Swingers met sponsored content at a bar a few years back and snagged its phone number, he might pin the number up on his calendar, but he would never call her. Ever. Because sponsored content lacked brains, beauty and charm.
But sponsored content – and content marketing in general for that matter – has come a long way from its origins as glorified and often ineffective native advertising. Today, Vince Vaughn’s character would take a look at sponsored content, hop up on the table, swing his shirt around and yell, “You know what big boy? You’re grown up. Cuz you’re growns up and you’re growns up and your growns up!”
While Vaughn’s sentiments will have once again obliterated the English language, his point would be well taken. Sponsored content has “growns up.” Publishers are taking sponsored content very seriously because it has become key to their financial lifeblood. Desperation leads to innovation, and experimentation – all good news for brands reluctant to part with traditional advertising dollars but that increasingly view mature sponsored content opportunities as a way to reach and influence target audiences.
In a recent interview, AOL Inc. CMO Allie Kline reaffirmed its view that content marketing is not advertising. While some of the campaigns she references stretch the limits of how we define content marketing, that is kind of the point; the definition is changing as the data, distribution and content becomes more sophisticated.
Sponsored content is one component of content marketing. Sometimes it is easily identifiable, while in other cases the sponsored content is cloaked within traditional editorial content. The latter development is a testament to the fact that display ads and other overt forms of online advertising are falling out of favor, and brands increasingly seek a way to have their content woven into earned editorial content, where it is less obvious to the reader, viewer, listener that the content is in fact “sponsored.” When was the last time you clicked on a banner ad? For me, it only happens when the web page I’m viewing shifts unexpectedly at the last second and causes me to click on an ad rather than the editorial content I actually wanted to read.
In our work with clients, we’ve been increasingly evaluating and making recommendations on sponsored content for technology brands. Based on this work, there are a few considerations brands should keep in mind when embarking on a sponsored content program.
Publishers are upping their game
Traditional publishers are no longer ceding the curated content game to agencies and other players in the market. Look no further than The Guardian, a well-known global publication that in 2014 launched Guardian Labs, an in-house branded content agency. Brands such as Silence Circle, a hot encrypted communications firm, chose Guardian Labs this year for a sponsored content program to promote the company. It is reported that Guardian Labs has 133 staff members, and there is no doubt that other publications will be closely watching efforts such as these to gauge whether they can launch similar efforts.
Similarly, QZ.com, an up-and-coming news and tech site, has teams of content, video and design experts working with brands such as HP on this infographic-anchored sponsored content, to build high impact sponsored content that will grab the reader’s attention. So what brands see today is a far cry from advertising and the full page “advertorials” that had an editorial flavor to them, but were still noticeably out of sync with a publication’s earned editorial content.
The details are in the fine print
TechCrunch, Forbes, Re/Code, CIO.com, you name the technology out let and most likely there will be a sponsored content option. Before selecting one or more outlets to work with, the brand should get answers to several key questions:
- Where will the sponsored content post direct the target? Some technology outlets will redirect users clicking on the sponsored content teaser to content that resides on the outlet’s site and looks and feels similar to earned editorial content on the site. The benefits to this approach
- What type of sponsored content works best? Sponsored content can, in theory, be self-promotional about a company or product, or it can be more traditional thought leadership whereby the goal is to attach the brand to a vision or market trend. While one could argue that self-promotional content can more directly link the target to a buying action, doing so makes the sponsored content more “ad” like relative to thought leadership content.
- What happens to the sponsored content post? A typical sponsored content scenario is that the teaser will appear in a vertical scroll within the top 10 news stories on a technology site. Brands must understand how long the content sits in that position, what happens to the content after it leaves the prime position and is shifted to another part of the site, and whether this content leads to another part of a site or an external landing page the brand (or publisher) most construct for this campaign. In some cases, a sponsored content piece might only run in prime position for one day, so understanding where the content travels to from there is key.
- Do they use CPM or fixed-fee model? In some cases, editorial outlets will use the ‘cost per thousand impressions’ fee structure, while in others it is a set fee determined by the publisher based on a broad range of factors. Each model has pro’s and con’s that should be evaluated.
Do listicles work for b2b brands?
List + Art (icles), otherwise known as listicles, have exploded on the b2c side of the house. Scroll through Yahoo News or any other consumer content site and you are bound to bump into some inane list along the lines of “Top 5 ways to pay off your mortgage,” “The 8 best places to eat fried chicken without a napkin,” or “Top 10 reasons you shouldn’t eat scallops.” How much these listicles contribute to society is debatable, but the listicles are eminently clickable and work reasonably well. For B2B sponsored content however, listicles remain a work in progress and must have a more substantive theme and valuable content that relates to the user’s pain points.
Does sponsored content work?
In January of this year, a blog post by SEO firm Moz did a fantastic job of analyzing the current state of sponsored content, and the potential for brands to see stronger results relative to advertising. In its “Content Promotion Manifesto,” Moz estimated that brands spent, on average, 6.7 percent of their content marketing budgets on sponsored content in 2013– and surely that figure has increased measurable since then.
In terms of effectiveness, the Moz blog post also cites a Contently survey of Internet users that reveals brands have a real opportunity to influence decision makers with sponsored content. Nearly half (48%) of respondents believe sponsored content that was labeled as such was paid for by an advertiser that influenced the content produced. The majority felt the “sponsored content” label meant something else.
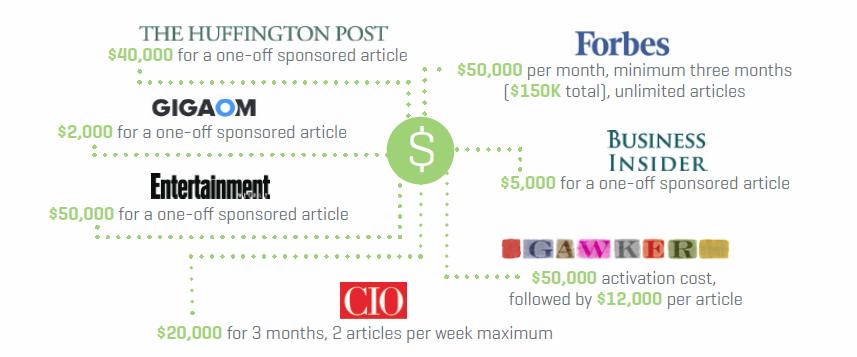
Equally encouraging is that the survey finds one-third of respondents are as likely to click on a sponsored article as they are to click on unsponsored editorial content. The Moz article also references a separate study that actually found consumers look more at sponsored articles (26%) than typical earned editorial articles (24%). Publishers have seized on the strong results and favorable consumer/business user data, charging brands five and six figure amounts for individual and limited-run campaigns (as the Moz chart below indicates).
The bottom line for brands evaluating sponsored content is to build a clear set of goals and objectives for the campaign, and identify the right partners to execute it.
Branding is no different than any other business investment. In the end, it comes down to return on investment.
The challenge is that with branding, ROI can be difficult to measure. You can look at increased sales. You can see an uptick in your social media and digital media analytics. One of the toughest questions to anwers, however, is if an acquisition were to occur, how much precisely is the purchase price affected by branding or even that a deal is in play because of brand investment?
What I can confidently say is that branding can contribute enormously. It can contribute to the possibility of your business being acquired and the value the ownership receives for the business.
Executives constantly question how a re-brand impacts enterprise value and the probability of being acquired. Here are some reasons that should open your eyes to the “why” of re-branding and the impact it can have on your enterprise.
Re-positioning. Through the lens of a rebrand could be a signal to the market that you are now an expert and market leader in the hottest and fastest growing market segments in your industry. This re-positioning exercise makes your business much more attractive.
Internationalization. In some cases re-branding is necessary so that a brand can also be used internationally. This may be because the brand name is too specific to a particular country. In certain countries a brand name may also conjure up the wrong associations. Organizations that sell the same products in several countries but under different brand names are also increasingly opting to use one brand internationally.
Bad Reputation. Bad reputations can have a serious impact on the enterprise value of a company. Re-branding can ensure that negative associations with the brand are forgotten or dispelled, both outside and inside an organization. This is the only way that a branding effort can remove any negative feelings about the brand.
Other reasons to re-brand include an outdated image or visual identity, or when a new CEO is put in place. These business changes usually have a desire to send a signal to the market that this isn’t your father’s Oldsmobile.
Bluetext has had quite a run of helping companies shape their brands as they position for growth and some type of liquidity event.
Some recent branding to acquisition stories can be found here:
Sourcefire Acquired by Cisco for $2.7 Billion (12 months after rebrand launch)
Sourcefire Case Study from Bluetext on Vimeo.
Acentia Acquired by MAXIMUS for $300 Million (4 years after rebrand launch)
Altimeter Acquired by Prophet (18 months after rebrand launch)
We recently launched some exciting re-branding efforts, including Cigital’s following their $50 million capital raise. The live website, the centerpiece of the branding effort can be found here. It will be interesting to see if our recent brand births eventually blossom into great acquisition stories. Are you next to be acquired? Lets talk about your brand and how we can help.
We get a lot of requests from companies of all sizes looking to “rebrand.” These requests can range from changing some colors and messaging, to completely overhauling a brand and website to address a new market or opportunity where the current brand identity may not be sufficient to address emerging corporate goals.
Enterprises across all industries face a lot of tough questions when deciding on the degree of their rebrand. Is the logo in play? Should the company consider a name change? Is there a mascot or other brand element that drives the culture? Have they gotten as far as they can with the current brand? Are there situations whereby they want to enter a new market and their current brand can actually be detrimental to future success?
To answer these questions we combine insights from both inside and outside the corporate walls, as well as the competitive environment and external market factors to define a path forward that helps them achieve their future corporate goals while addressing different budgetary requirements.
Sometimes there are brand elements that are so ingrained in the culture that tough decisions emerge. A great example was the first time we were asked to rebrand Sourcefire. Sourcefire rose to fame with the commercialization of its open source intrusion detection software product Snort in the 2000s. The product included a massive community of loyal and dedicated supporters who were passionate about Snort and its technical capabilities. They helped the company grow in terms of revenues and fame, and were closely aligned with the company’s mascot Snorty the Pig.
Snorty the pig was always associated with the brand, and all marketing materials including an annual calendar were very popular across the IT security community.
They engaged the Bluetext team to drive legitimacy for the company and brand as they looked to diversify their revenue base into Government. This was a new audience and there was a feeling that the Snort Pig mascot and company attitude would not play well. Following a thorough discovery process our recommendation was to tone down Snorty without eliminating him from their marketing efforts. Our goal was to present the brand as more stable and conservative. The results were tremendous. When they came back to us three years later to rebrand again, Snorty was playing a significantly less prominent role but they continued to leverage the pig in ways to embrace the old while expanding into new markets. The rest for Sourcefire is history as they were sold for $2.7 billion to Cisco in 2013.
The lessons learned from Sourcefire are quite valuable. Many factors need to be assessed to measure the value of your brand equity with your current and prospective customers, including search equity, brand equity and association, and name recognition. If your current customers are loyal and you are in a position of strength with them, but you need help entering a new market, they should understand the reasons for the rebrand and what it means to them without disrupting their relationship with you.
As brands mature, what has gotten them to one point may not be the best path to get to the next level. Many factors should be addressed. Weigh the pros and cons, and don’t make judgments based on gut. Look at the market, assess the opportunity, and make sure to give your brand the best chance at long term success. While you may be succeeding in many categories, it is possible that you have to take a step back in order to move forward. Here are six questions that must be answered when embarking on a “rebrand” effort:
1. How will this rebrand impact current customers?
2. Have you taken this brand as far as it can go?
3. How will your current brand play with prospective customers in new or adjacent markets?
4. Have you thoroughly analyzed the market to see what the outside world thinks about our brand and market positioning?
5. Are you positioning around how customers search for and consume products or services, or how you internally orient your business?
6. Do you want to zag if all of your competitors zig?
A rebrand effort can come in many shapes and sizes. Make sure you do a thorough assessment of your needs and growth opportunities, as it is critical to never disrupt your business as you embrace the market through a rebranding effort.
We have leapfrogged almost overnight from a digital first to mobile first multi-screen world.
Brands – no matter their size – can no longer afford to ignore the mobile market. Users aren’t just browsing on mobile devices – they are now finding content, sharing it socially and completing purchases at a rate that is increasingly on par with their older desktop siblings – and this is now having significant implications on website design.
Where responsive design was the new frontier not more than 18 months ago – most progressive digital studios have adopted a mobile first design mentality. Instead of designing websites for desktop users and degrading the experience and functionality for mobile – they are now starting with the mobile screen as their primary palette and adding layers to ‘dilute’ the experience for desktop and larger screens.
Putting mobile at the front of the website design process leads to sites that are simpler, faster, more usable and – most importantly – more accessible to your customers. Here are the five primary keys to a smart, mobile first design strategy.
Speed
With users – and Google – demanding sub-one-second page loads – speed is a critical component of mobile first design methodology. As a result, you will be seeing a lot more sites going to a flat, 2D design with single blocks of color and streamlined images.
Navigation
Navigation is a major consideration for mobile website design, so we’ll be seeing more brands using fixed menu bars and infinite scrolls for continuous access and loading of content…and of course the ‘hamburger’ menu with three horizontal lines is now almost ubiquitous.
Typography
Since the days of newspapers – type has always been a good way to show the visual hierarchy of page elements. But in a mobile first world, readability is critical, so many brands are using a wider range of larger fonts that better render text as easily visible on smaller screens.
Layout
A desire to cater to mobile users has led to a variety of new layout trends, including tile or grid-based layouts where the content shifts to accommodate different dimensions, displaying single or multiple tiles depending on the screen size. Parallax scrolling to make page elements shift or disappear is also seen as a cool and sophisticated trend in mobile design.
Usability
The last – but far from least – consideration is usability, which brings everything together to optimize how much content can actually be consumed on a smaller screen through gestures, taps, swipes and clicks to get to more content faster. This is huge push for the Google search engine algorithm, so companies whose audiences are coming in via their mobile devices need to understand how important mobile usability has become.
Don’t let your content get left behind in a cloud of mobile dust – or worse yet – your brand annihilated by ‘Mobilegeddon’…don’t be last to mobile first.
The Challenge:
A leading scientific association came to Bluetext with a unique challenge. The association’s goal was to drive higher click-through-rates (CTRs) for its core web properties without altering the front-end design of each site before 2016. Built on a custom, legacy CMS, these sites featured an aged look and were not built responsively. The Bluetext team knew immediately that there was one way to boost traffic to these properties in an effective, long-term fashion that would simultaneously increase conversion rates to purchase, and grow overall engagement with the association’s premium content. Bluetext mapped out a highly-detailed Search Engine Optimization (SEO) Strategy for each of these properties and executed it methodically through the first half of 2015.
Tactics
Our team ran a series of detailed reports on these web properties’ performance in search, analyzing every factor that could possibly be weighing the site down. When assessing SEO rankings, it is key to remember that a website’s “domain authority” is impacted by two main audiences: the search bots crawling the website, and the people searching it and reviewing its content.
Bluetext crafted a multi-phase plan that aimed to improve perceptions of the web properties among both audiences, making sure that any changes made to appeal to crawler bots also suited the needs and expectations of live searchers. Bluetext made recommendations for highly-relevant short and long-tail keywords to include in meta data and content across the site. We then pointed out specific pages on the site that housed meta data (titles, descriptions, URLs) that was too short or too long- and harmed the sites’ search “scores” by breaking structural rules. Bluetext collaborated with the association to rewrite meta data so that it fit Google and Bing’s structural guidelines, and also incorporated keywords that would draw the right searchers to relevant pages, thus boosting overall search authority.
Our next step was to assess website speed and load, and to point out specific tactics to improve these metrics and optimize the user experience. In comparing these web properties to competitors, we found specific referring domains that the client could form relationships with to gain backlinks and grow trustworthiness. Our team explored the client’s social media activity in-depth on platforms that could be used to strengthen relationships with their target audience. We sat with the association’s marketing team and pointed out opportunities to broaden awareness of events and useful materials, and to stimulate engagement among members with posts that ask questions or offer a short piece of valuable information. And since we are a digital design agency and we couldn’t quite help ourselves, we offered design insight on how to effectively rearrange the homepage to improve CTRs to interior pages and display timely, relevant content without drastically changing the current design.
Execution
After receiving a green light from the association to make the recommended changes to their web properties, we got straight to work. Using Google Analytics and Webmaster Tools to identify pages that served as the top 75 “entry points” to the organization’s largest domain, we recreated meta titles and descriptions for these pages so that they fit structural guidelines and utilized keywords that are heavily searched on a monthly basis.
To grow breadth and depth of keyword usage on the sites, our team filled in “Alt Tag” descriptions for images. We looked back at periods where web traffic sharply declined or increased, pinpointing dates when the search algorithm changed and caused these fluctuations. Since the overall quality of a business or association’s Wikipedia profile plays a strong role in search rankings, we combed through the client’s Wikipedia properties and elegantly filled them with high-volume, specific keywords. To draw a closer relationship between the pages across a large site, we created a highly-detailed internal linking strategy that mapped many high-volume keywords on interior pages to particularly relevant interior pages in other areas of the site.
We extended our recommendations to the client’s properties in other countries, identifying ebbs and flows in traffic to these other sites and noting vital changes that should be made to site structures. We also compiled a set of recommendations for the client to manipulate the current mobile design without making major changes so that mobile and tablet users could have a more pleasant user experience.
The Outcome
The time and effort spent by Bluetext to optimize search for this association’s web properties made a drastic impact. Total traffic to the largest site in early June was 13X larger than original average traffic to the site. This same domain saw 12X the number of users visiting the site by early June, alongside a 500% growth in the number of users visiting the property on mobile and tablet devices since project inception. User engagement with website content also increased through project conclusion, with users visiting each page for 20 seconds longer than before. This association is now getting the website CTRs that it deserves with a design that remains almost entirely untouched.